Cyberattacks on Local Governments on the Rise, Highlighting a Need for Enhanced Security
What would a cyberattack on your local government look like? Drata analyzed threat trends to break down the growing issue.
Computer servers run by the city of Dallas were found to be infected with malware on May 3, 2023, spurring staff to begin shutting off computers to prevent its spread.
The effects of the attack were sprawling, including hits to police and public courts, hampering residents' ability to report nonemergencies to the city's 311 service, leaving people unable to pay water bills online, and taking the city's public library system offline. One month later, the city reported most, but not all, services had successfully been restored.
Private sector employees may be understandably focused on how cyberattacks can affect their employer and the private data their company keeps on them. But in today's geopolitical environment, hackers are increasingly targeting governments to sow chaos and rake in profit.
Drata analyzed threat trends from BlackBerry, the FBI, and credible news reports to illustrate the increasing threat posed by cyberattacks on local governments and the public sector. Local government is sweeping and includes services like law enforcement, public health services, 911 call centers, and educational organizations—as well as departments providing important business functions like permitting and code enforcement.
The attacks themselves can be lucrative and are conducted by groups bent on one-upping each other with larger and grander victims they can boast about.
In one of the most disruptive forms of cyberattack, ransomware is installed on a computer system, encrypting and locking it so it cannot be accessed until a ransom fee is paid. And the cost for a public sector organization to contain and secure systems after an attack can average $2.6 million in 2023, up from $2 million the year prior, according to IBM's 2023 threat report.
In Dallas' case, the city has taken months to navigate May's ransomware attack. The city council approved spending $4 million on threat detection services in the aftermath and proposed an additional $9.7 million in its forthcoming budget for more security. The city is also footing the bill for credit monitoring for people whose data was affected, which includes everyday citizens.
Singling Out Government
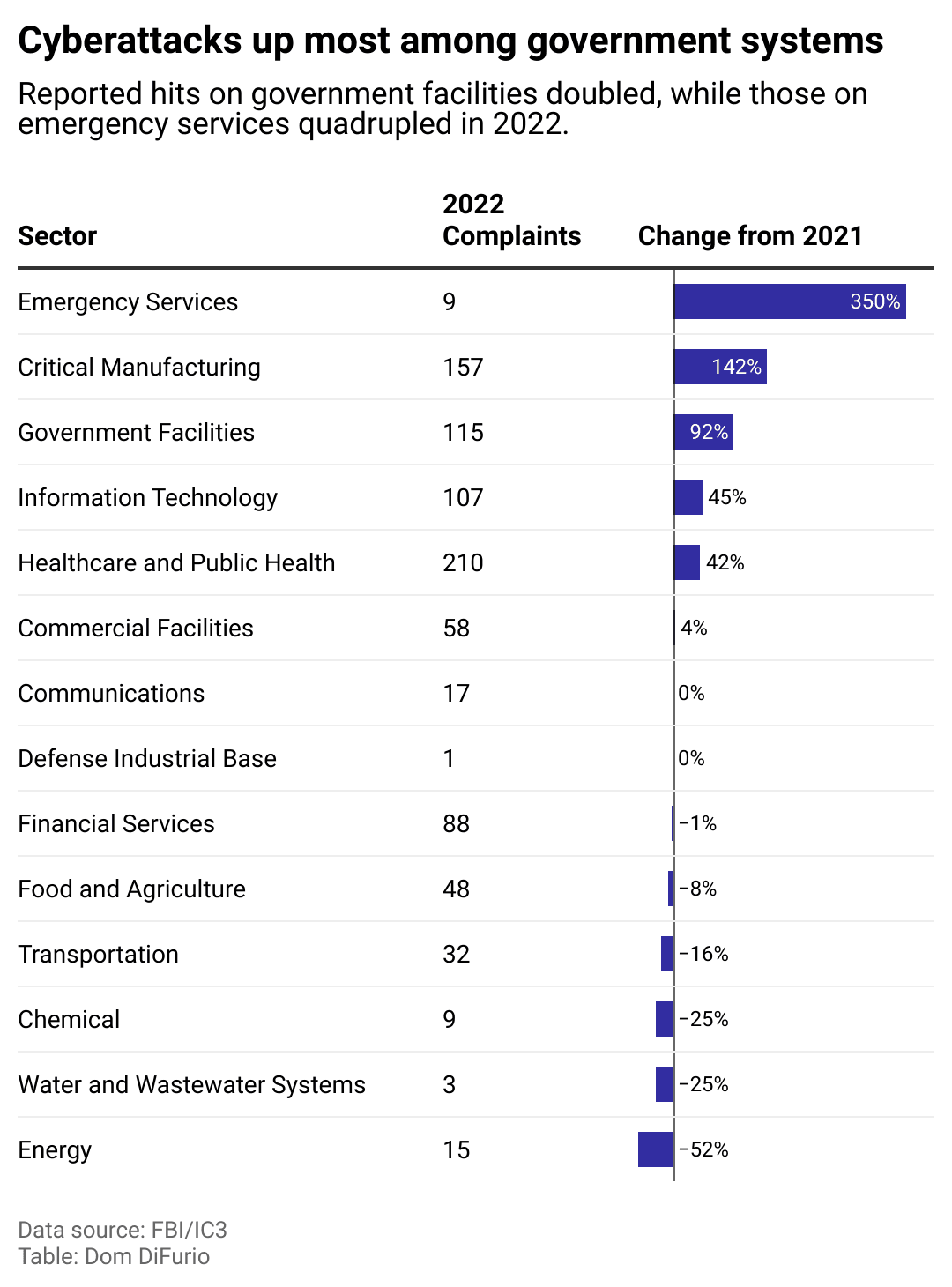
Attacks on government facilities nearly doubled from 2021 to 2022, according to data kept by the FBI's Internet Crime Complaint Center.
There is some evidence that governments are beginning to prioritize the prevention and mitigation of these breaches. From 2018 to 2020, the share of state governments outsourcing their cybersecurity resources dropped from 60% to 43%, according to a Deloitte study of government cybersecurity preparedness. The firm advises that organizations with dedicated in-house workers are better equipped to manage security threats.
Still, state governments comprise only a small fraction of the tens of thousands of local governments that serve as potential targets for cybercriminals and foreign nations.
And the repercussions often extend beyond the attacked organization and its employees.
In Dallas' case, city workers have voiced concerns about their children's private information being among the data stolen by criminals, leaving minors vulnerable to identity theft and damage to their credit and financial potential once they become adults.
Nearly 90,000 Soft Targets Nationwide
Public and private sector experts agree local governments are an appealing target due to their numbers—and because they are often under resourced to handle ransomware and other forms of cyberattacks. By one estimation, there are nearly 40,000 cities, towns, and townships and around 50,000 special government districts nationwide.
The authors of the first-ever nationwide survey of local governments' cybersecurity practices just before the COVID-19 pandemic identified "a lack of cybersecurity preparedness within these governments and a lack of adequate funding for it."
The federal Cybersecurity and Infrastructure Security Agency, also known as CISA, released a strategic plan in August 2023 declaring "too many American organizations are soft targets" and calling for state and local governments as well as tribal and territorial governments to harden their IT systems.
Local government attacks grew so much in 2021 that the FBI issued a memo the following spring warning that local government had become the second most-targeted entity behind academia.
The implications can be potentially life-threatening when considering the services our local governments control. The memo cites attacks taking down COVID-19 vaccination efforts and suspending county computer systems.
In 2023, just 14% Percent of Local Governments Collaborated Against Threats
A consortium of local governments working together to thwart cyberattacks has existed for at least 20 years—yet only about 14% of governments, or 13,000 of them, have opted to take part, according to CISA. The organization, called MS-ISAC, has also noted publicly that opting in is only part of the battle; staying engaged with all members to share best practices and techniques is an ongoing effort.
The organization hosts regular webinars and sends out threat alerts to keep partners vigilant against vulnerabilities in software that emerge.
Why Paying Up Doesn't Pay When it Comes to Ransomware
Federal authorities most often recommend against paying a ransom to attackers because there is no way to assure the criminal will act in good faith and destroy the stolen data in return.
Doing so could also "embolden" the criminals to target other organizations, according to the FBI.
Analysis of cyberattacks from IBM reveals paying the ransom in the case of a ransomware attack doesn't make financial sense, either. Not including the ransom amount itself, organizations that paid a ransom spent about 2% less to mitigate the attack than organizations that didn't, according to IBM. But if the ransom was high, on the order of several million dollars, that cost could easily outpace the small potential savings.
Instead, data suggests incorporating automation into cybersecurity measures can help lower mitigation costs after an attack. Organizations leveraging automation were able to handle attacks in 16% fewer days—with accordingly lower personnel expenditures—than organizations that did not incorporate automation.
Rather than paying ransoms, experts also recommend governments approve greater funding for cybersecurity as well as improve policies and generate a culture that considers security at all levels of staff.