Compliance and Privacy Frameworks, Automated
Automate evidence collection and tests, manage multiple frameworks simultaneously without added effort, and achieve continuous compliance.
Automate evidence collection and tests, manage multiple frameworks simultaneously without added effort, and achieve continuous compliance.
Before Drata, meeting compliance and privacy regulations and requirements was an arduous and manual effort. With hundreds of integrations that power Drata's automation, we can take you from security novice to continuous monitoring in a few hours. With 20+ pre-built frameworks and easy-to-use tools to build custom frameworks, your team will thrive through the GRC process.
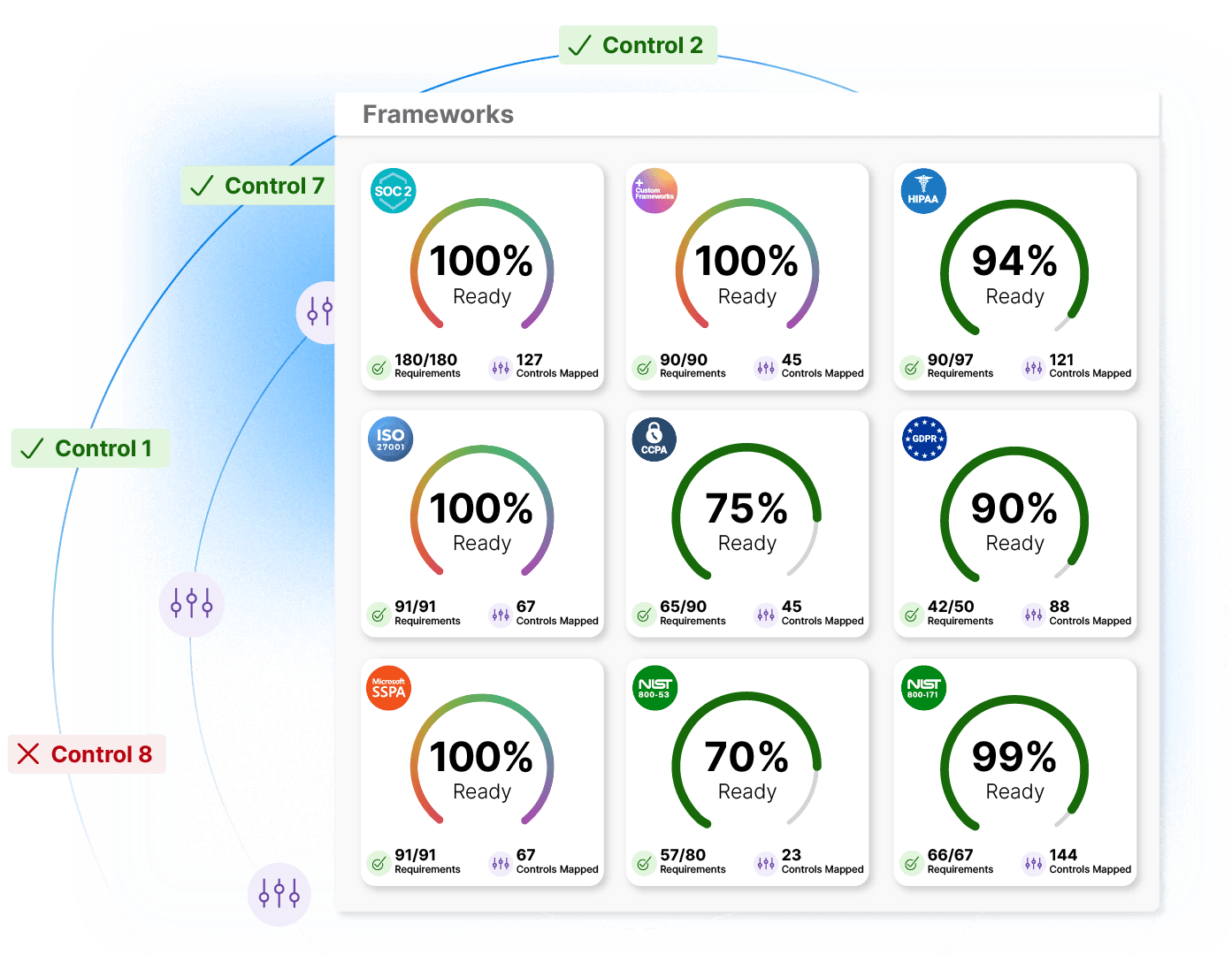
From startups to enterprise companies, Drata scales with you. With a library of built-in controls and standard framework requirements, we empower teams to rapidly deploy frameworks without prior experience—all with the customization and flexibility needed by GRC pros, such as custom controls and frameworks. Whether you’re pursuing ISO 27001 or need to manage multiple frameworks, you only need to do the work once.
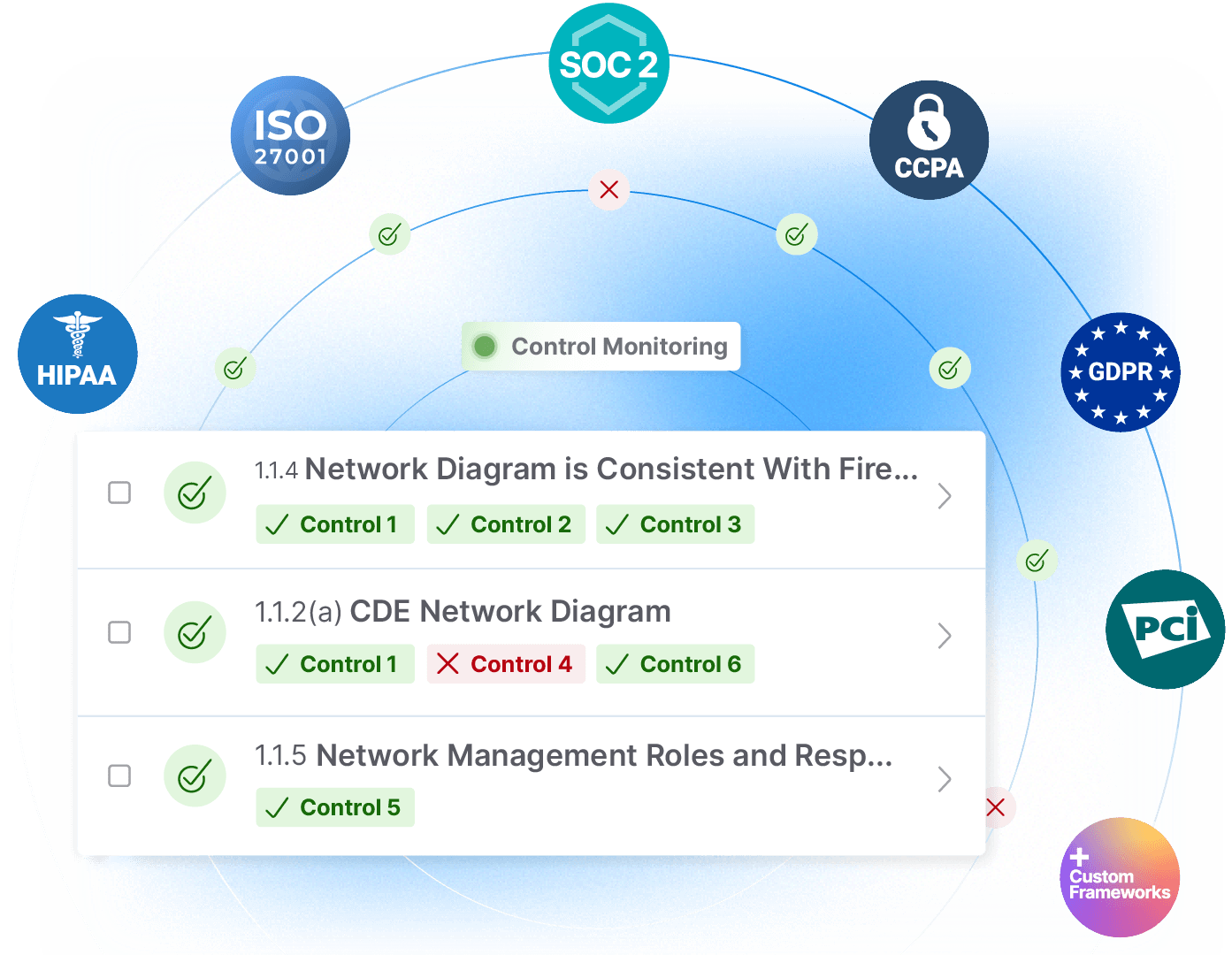
Drata's automated continuous control monitoring gives you a complete view of your compliance status at all times. Refocus on business objectives knowing that Drata is always working behind the scenes collecting evidence for your GRC processes and audits across your entire tech stack through hundreds of integrations. The platform helps you prioritize issues that need to be addressed to manage your security posture proactively.

20+ Supported Frameworks
Drata's control mapping means any compliance framework, standard, or regulation is available at your fingertips—yes, even custom ones you may need to create.

SOC 2 defines criteria for managing data based on: security, availability, processing integrity, confidentiality, and privacy.

ISO 27001 is an information security management system (ISMS) that helps keep consumer data safe.

HIPAA is a law requiring organizations that handle protected health information (PHI) to keep it protected and secure.

GDPR is a regulation in EU law on data protection and privacy in the European Union and the European Economic Area.

PCI DSS is a set of controls to make sure companies that handle credit card information maintain a secure environment.

Cyber Essentials helps companies guard against the most common cyber threats and demonstrate commitment to cyber security.
Safely navigate the implementation and usage of artificial intelligence with this risk management framework.

CCPA gives consumers control over the personal information that businesses collect and guidance on how to implement the law.

CMMC is a unified standard for implementing cybersecurity across the defense industrial base (DIB).

SSPA sets privacy and security requirements for Microsoft suppliers and drives compliance to these requirements.

National Institute of Standards and Technology’s framework for Improving Critical Infrastructure Cybersecurity (CSF).

NIST SP 800-53 is a catalog of controls for all U.S. federal information systems except those related to national security.

NIST SP 800-171 recommends requirements for protecting the confidentiality of controlled unclassified information (CUI).

ISO 27701 specifies requirements for establishing and continually improving a privacy information management system.

The FFIEC provides a set of technology standards for online banking that financial institutions must follow.

The Cloud Controls Matrix by Cloud Security Alliance (CSA) is a cybersecurity control framework for cloud computing.

FedRAMP compliance and authorization enables SaaS companies (referred to as CSPs) to work with federal government agencies.
NIS 2 Directive is a EU-wide cybersecurity law that improves the resilience and incident response across the European Union.

Digital Operational Resilience Act (DORA) ensures EU financial entities are resilient to information and communication technology (ICT) disruptions.

ISO 42001 is an international standard that provides guidelines for organizations to manage their AI systems responsibly and effectively.
Frequently Asked Questions About Supported Frameworks
What frameworks do you currently support?
Drata supports 20+ frameworks, plus you have the ability to create custom frameworks. We currently support SOC 2, ISO 27001, HIPAA, GDPR, PCI DSS, CCPA, Microsoft SSPA, ISO 27701, NIST CSF, NIST 800-53, NIST AI RMF, CMMC, FFIEC, SOX ITGC, NIST 800-171, ISO 27017, ISO 27018, Cyber Essentials and your own custom frameworks.
What if requirements change for frameworks?
As frameworks adjust requirements, we take care of ensuring the Drata platform has all of the latest requirements so you don't have to keep up with the changes.
Automate Your Journey
Drata's platform experience is designed by security and compliance experts so you don't have to be one.
Close more sales and build trust faster while eliminating hundreds of hours of manual work to maintain compliance.