HIPAA Compliance: How Healthtech Companies Can Remain Compliant
HIPAA compliance can be complicated. That’s why we created a comprehensive guide for health technology companies to achieve, and stay compliant.
HIPAA compliance has become increasingly complicated due to new technologies and emerging software in the healthcare industry. Nearly all healthtech companies (whether large or small), are responsible for their patients' privacy and security at industry-level standards.
So, what exactly does HIPAA stand for? What does your business need to know about getting — and staying — compliant? Get all your burning questions answered in this comprehensive guide below.
What is HIPAA?
HIPAA (Health Insurance Portability and Accountability Act) of 1996, is a federal law in the United States that regulates the protection of health information.
In summary, it outlines many different security and privacy requirements, which are needed to manage protected health information or PHI—health data that can be linked to a specific person as it includes:
Name, place, and date of birth
Biometric identifiers
Vehicle identifiers
Social security numbers
Payment information
Contact data
Photos
Protecting PHI is more vital than ever, primarily due to the rise of cloud computing and growing digital infrastructure in the healthcare sector.
Why Does HIPAA Compliance Matter?
Safeguarding protected health information (PHI) is necessary for any businesses handling private health data and seeking to build trust.
HIPAA applies to any company that deals with Protected Health Information (PHI), physical or electronic, including health records, health histories, lab test results, medical bills, account numbers, images, and more. You must comply with HIPAA regulations if you are a covered entity or business associate (or vendor).
Examples of covered entities:
Doctors
Clinics
Psychologists
Dentists
Nursing homes
Pharmacies
Health insurance firms
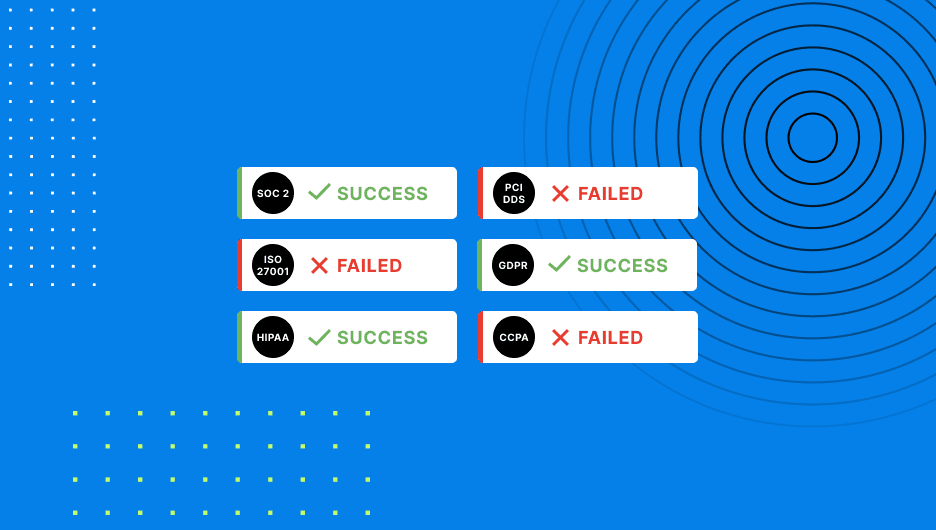
Meeting all HIPAA rules and regulations needs a mix of internal procedures, appropriate technology, and strategic external relationships. Failing to comply can be extremely costly to your business, however there are a few best practices for health technology entities to remain HIPAA-compliant (continuously).
Let's dive into what’s needed to make your health technology software HIPAA-compliant.
HIPAA Compliance Requirements
The U.S. Department of Health and Human Services (HHS) takes compliance very seriously. Understanding the HIPAA requirements—including technical, organizational, and administrative standards—is critical for shaping your company’s security practices.
Privacy Rule
Health technology organizations must establish fair boundaries on using and disclosing PHI.
According to the HHS standards, the privacy rule means:
“The Privacy Rule generally requires HIPAA covered entities (health plans and most health care providers) to provide individuals, upon request, with access to the protected health information (PHI) about them in one or more ‘designated record sets’ maintained by or for the covered entity.”
It also means having well-documented security and privacy policies and procedures, a good training program which includes privacy requirements, and enforcing best practices with your infrastructure provider and vendors, among other things. This would include:
Implementing documented policies, procedures, and behavior standards.
Using business associate (BA) agreements.
Having a procedure for filing complaints.
Maintaining all documentation, paperwork and recording retention.
Enforcing retaliation protection.
Security Rule
The HIPAA Security Rule has several security standards divided into the categories of administrative safeguards, physical safeguards, technical safeguards, organizational requirements, policies and procedures, and documentation requirements.
More specifically, the rule requires health technology organizations to maintain written security policies and procedures by following recommended practices like:
Access control (Implementing two-factor authentication for all users)
Audit controls (Having procedures in place to determine when security violations occur)
Identity management (Using a verification system to double-check a user’s identity)
Transmission security (Ensure networks are fully encrypted and maintain firewalls)
Integrity (Provide breach alerts and ensure all data have not been improperly altered)
Breach Notification Rule
The HIPAA Breach Notification Rule outlines the steps to take in a data breach. While no system is completely secure, businesses should ideally have a clear strategy for what to do in an emergency.
If a breach occurs, your company must tighten controls or update processes to ensure that it does not happen again. Best practice Breach Notification procedure involves:
Notifying affected patients.
Provide public transparency.
Disclose data breaches within two months.
Staying HIPAA compliant and providing assurance means continuously monitoring controls. At the same time, teams must ensure that all communications protect PHI.
4 Best Practices for Continuous Compliance
Meeting HIPAA standards is an ever-evolving challenge—and if you don’t have the right processes in place to monitor, alert, and automate, it can be hard to keep up with. For health technology companies that stay compliant, it starts with these best practices below.
Employee Training
Annual company-wide training is a great way to empower employees to stay up-to-date with HIPAA rules and regulations. As a requirement, every health-related business must train their employees at least once per year in compliance and cybersecurity.
Implementing Security
In addition to employee training, companies should also embed access controls and ensure maximum security to reduce the likelihood of data breaches. Using compliance technology software, companies can also strengthen the security of their facilities as well as devices.
Risk Assessments and Auditing
Your team should perform regular risk assessments and internal audits. To do this, companies should set up risk assessments for things like unauthorized file transfers, account logins, or access or modification of data, controls, or configurations.
Detailed Documentation
Lastly, each policy and process that is created to protect PHI, should be documented in your company for at least six years. This includes documentation records of all privacy policies, complaints, remediation plans, among other documentations.
Non-Compliance HIPAA Risks
Security breaches happen to everyone, and most will be out of your control. What matters most for compliance is transparency—what happened, how it was resolved and how quickly, what systems were impacted and how major was the breach?
Make sure you have detailed records and evidence that shows how you handle incidents when they happen, if your company fails to comply, there could be costly consequences.
Monetary Penalties
The consequences of HIPAA violations are significant and far reaching. Non-compliance can cost healthcare organizations up $50,000 per incident up to a maximum of $1.5 million and including criminal charges.
Reputational Damage
Building a reputation can take years, but it only takes one incident to damage one’s reputation permanently. Your company’s reputation can be ruined after a significant data breach if one’s cyber security is not above industry standard.
Loss of Trust
Most importantly, repairing that reputation can take far longer than the actual breach itself. Customers, patients, and industry partners can easily lose confidence and decide to distance themselves if they no longer feel safe entrusting their records with an organization.
Simplifying HIPAA Compliance
HIPAA compliance can be costly for most companies if not managed continuously.
No matter the circumstance or stage you are at, all healthtech companies are responsible for protecting patients' privacy and security at the highest level. At Drata, we help make compliance simpler and easier to manage.
We provide customizable HIPAA-specific policy templates and HIPAA-approved employee training directly in the platform, Drata creates a single source of documentation. As businesses grow, teams can map current HIPAA controls to new frameworks, reducing duplicate work.
Everything we do is designed to take as much burden as possible off your teams while maintaining compliance.
Because once you’ve done all that work to become compliant, you’ll need systems in place to help you stay secure and compliant and prove it.
If HIPAA compliance is on your horizon, it’s a good time to take a look at automation with Drata.