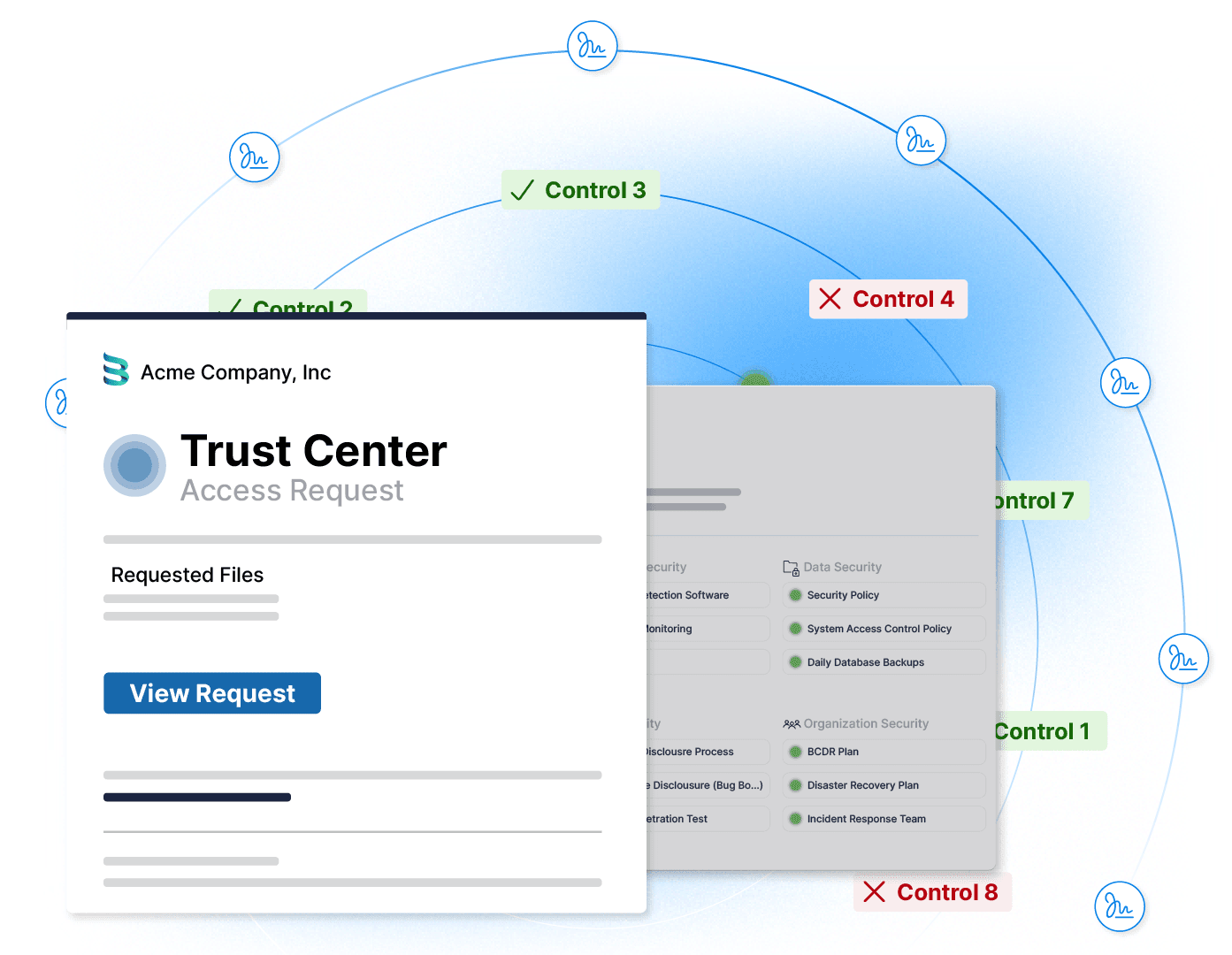
Security at Drata
Trust is everything to us, but you can’t have trust without security. That’s why we use independent experts to verify our security, privacy, and compliance controls. No company is impenetrable, and we're always aiming to be better. If you find any security issues with Drata, please report it.