HIPAA Compliance Checklist: Essential Steps for Compliance
Use our HIPAA compliance checklist to build a program that preserves patients’ privacy and keeps their medical information secure.
When you go to the doctor, you expect your private medical information to be kept confidential. The Health Insurance Portability and Accountability Act of 1996 (HIPAA) makes that expectation the law. Any organization receiving, storing, transmitting, or processing protected health information (PHI) must keep that information both private and secure.
Achieving HIPAA compliance requires you to evaluate almost every aspect of your business operations. To help you get started, we drew on our compliance monitoring experience to create this HIPAA compliance checklist.
Use it to build a program that applies reasonable measures to preserve patients’ privacy and keep their medical information secure.
HIPAA Compliance Checklist for 2023
How you achieve HIPAA compliance depends on how your organization handles PHI.
What kind of PHI do you have and in what quantities?
Do you manage PHI entirely within your systems?
Do you exchange PHI with other businesses?
Keep these questions in mind as you use our HIPAA compliance checklist.
1. Form a Compliance Team or Function
Create a dedicated compliance team that includes stakeholders from across the organization. Your IT and legal departments will play critical roles, but every department that deals with PHI has a role to play as well.
Hold each compliance team member accountable for specific, assigned responsibilities. When forming your team, it’s important that they read and understand the HIPAA rules—Privacy, Security, and Breach Notification—inside and out.
Here’s a quick refresher on the difference between the two:
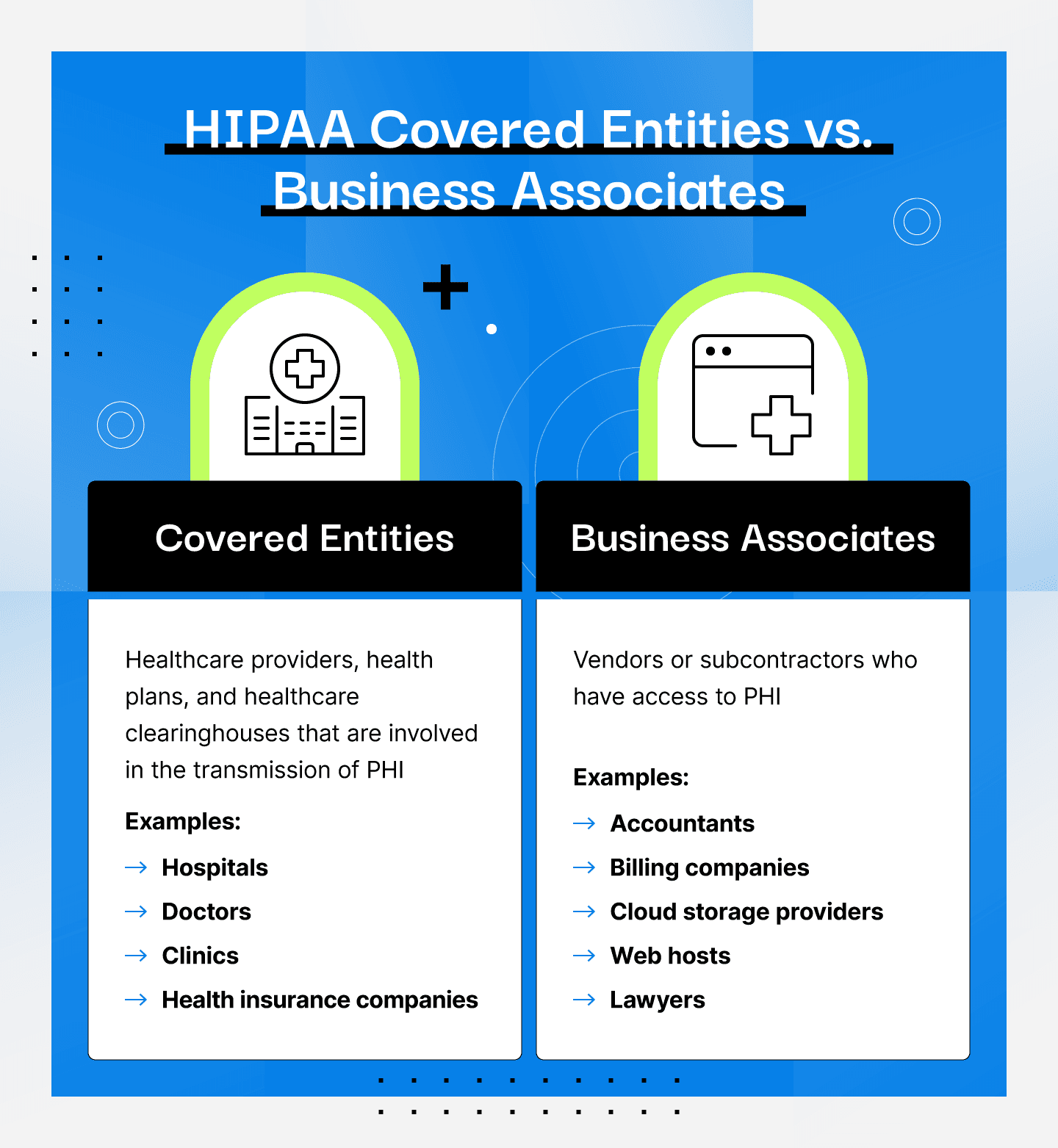
Covered entity: health plans, healthcare clearinghouses, and healthcare providers who electronically transmit health information for transactions that the Department of Health and Human Services (HHS) has set standards for.
Business associate: vendors or subcontractors who have access to PHI such as accountants, billing companies, cloud storage providers, web hosts, lawyers, etc.
2. Conduct a HIPAA Risk Assessment
There are three approaches to evaluate organizational risks.
An asset-based approach would look for weaknesses in the organization’s databases, servers, and network infrastructure that could expose PHI.
A vulnerability-based assessment would consider ways PHI could fall into the wrong hands, whether accidentally or through a cyberattack.
A threat-based approach would focus on identifying and evaluating the threats to an organization's assets.
Whichever approach you take, the HIPAA risk assessment should identify and prioritize risks based on their impacts and probabilities. This is a required step for both covered entities and business associates to comply with the HIPAA Security Rule.
3. Develop a Compliance Plan
Build a compliance plan by aligning your prioritized risks with the administrative, physical, and technical safeguards that the HIPAA Security Rule requires.
Administrative safeguards include security risk management processes, access controls, training, and incident response planning.
Physical safeguards include measures that control physical access to your network infrastructure and endpoints.
Technical safeguards include the hardware and software that control and monitor PHI access as well as protect PHI at rest and in transit.
4. Implement Your Plans Internally
Establishing HIPAA compliance safeguards and mitigating risks will require contributions from everyone in your organization. It goes beyond installing new firewalls and changing locks on the server room. How your employees use or share PHI must align with HIPAA’s requirements—which may mean changing how people work.
That’s why it’s crucial to have executive leadership buy-in. They can help set priorities across the organization to aid with the implementation of new processes.
Your compliance team will need support at every level, from management to frontline workers. That can only happen if your leadership team constantly reinforces the importance of HIPAA compliance.
5. Determine Which Vendors Must Sign a Business Associate Agreement
As you change your internal processes, you must also ensure compliance from any business associate that may encounter PHI. Consulting physicians or medical records processors are obviously subject to HIPAA. But don’t overlook cloud service providers, law firms, and other third-party services.
Once you’ve identified all business associates you work with, you’ll need to create a business associate agreement for them to sign. These agreements are crucial to ensuring your business associates are following all HIPAA rules when working with PHI.
Once a business associate agreement is in place, it will remain valid unless the agreement is terminated or regulatory changes occur. This is why it’s a good idea to periodically conduct a third-party risk assessment to align your business associates with your compliance policies.
6. Report Data Breaches Immediately
Your compliance team must assume that PHI breaches can happen at any time and prepare accordingly. In particular, their incident response plans must address HIPAA’s Breach Notification Rule.
Any time unsecured PHI leaves your control, you must directly contact all patients affected by the breach. Written or emailed notices must go out within 60 days of the breach’s discovery. If direct contact is not possible, you may need to post notices on your website or in local newspapers.
The Breach Notification Rule also states that notices to patients need to be written in plain language. These notices should include:
An explanation of what has happened
A summary of the information has been exposed or stolen
A brief explanation of what your organization is doing or has done in response to the breach
A summary of the actions you will take to prevent future breaches
Instructions for how breach victims can limit harm
You must report all breaches of unsecured PHI to the HHS. Report large breaches affecting more than 500 people within 60 days. An annual report to the HHS can summarize smaller breaches.
HIPAA requires media notifications of large breaches, so make sure you are ready for some bad publicity. Although not included in HIPAA regulations, you should also prepare to report breaches to law enforcement, state or local regulators, and business partners.
Download HIPAA Compliance Checklist PDF
We’ve created a HIPAA compliance checklist resource to help you kick off your HIPAA compliance journey.
What Is HIPAA Compliance?
HIPAA provides the regulatory framework for protecting patient privacy in the United States. As you would expect, these regulations apply to healthcare providers, insurers, and health data clearinghouses. However, any other company these entities share PHI with are considered HIPAA business associates and will be subject to the same regulations.
The law requires that organizations take reasonable and appropriate measures to protect patient information. “Reasonable and appropriate” will mean different things in different contexts. For example, a doctor’s solo practice may care for several hundred patients, while hospital systems treat hundreds of thousands of patients every year. A law firm may only handle a few cases per year that involve PHI.
All must comply with HIPAA, but they will comply differently. HIPAA compliance is not a one-size-fits-all standard.
In fact, the Security Rule has a section called "Flexibility of Approach" that encourages organizations to decide which security measures to implement based on the following factors:
The size, complexity, and capabilities of your organization
Your organization's technical infrastructure, hardware, and software security capabilities
The costs of security measures
The likelihood and impact of potential risks to electronic PHI
Tips To Achieve and Maintain HIPAA Compliance
Preserving the privacy of patients’ medical information requires a never-ending focus on security. Keep these six tips in mind as you build out your HIPAA compliance program.
Monitor Compliance Continuously
Achieving compliance only means you had PHI under control at an instant in time. Anything could happen after that to expose PHI—someone may lose a laptop, hackers could breach your defenses, or an unqualified employee could accidentally receive PHI they shouldn’t have.
HIPAA compliance is a process, not an event.
The only way to stay compliant is by continuously monitoring your security controls and developing total visibility into your security posture.
Train Employees and Reinforce Best Practices
Technical risk may not be the biggest threat to HIPAA compliance. You need to account for the human factor. Employees, consultants, and other agents who access your organization’s PHI must understand the importance of HIPAA, including:
Why patient privacy matters
Their compliance responsibilities
The consequences of HIPAA violations
Your compliance team must develop a training program that raises awareness of your HIPAA compliance efforts. New hire onboarding and annual refresher sessions may be sufficient most of the time.
However, the compliance team may identify situations—such as mitigating breaches or addressing new regulations—that require additional training.
Stay Current With HIPAA and HHS Updates
Congress regularly updates HIPAA to address emerging privacy risks. Even without legislation, HHS updates to existing rules may impact your organization’s HIPAA compliance. Monitor the evolving HIPAA landscape to understand how your organization should adapt.
Compliance partners with deep expertise in HIPAA can flag changes impacting your compliance status, giving you time to address any new risks.
Minimize Access to PHI
During the journey to HIPAA compliance, organizations often find that too many people have easy access to PHI. Over-permissioned accounts make breaches and HIPAA violations almost inevitable.
Apply role-based, least-privileged access policies that limit PHI access to the people who need it when they need it. You can also plan to conduct regular access reviews to ensure that only those who need access to PHI to carry out their job duties have it.
Eliminate Duplicate PHI
PHI risk increases when you store identical medical records in multiple locations, such as in different databases or on employee laptops. The more places you keep PHI, the more opportunities for that information to fall into the wrong hands.
The best way to limit PHI risk is not to have it in the first place.
An electronic health record (EHR) system centralizes PHI storage and distribution. Rather than storing permanent copies of medical records in multiple systems, EHRs can transmit data on a just-in-time basis.
Always Encrypt PHI
Keep PHI encrypted at all times, whether at rest or in transit. Strong encryption makes data impossible to extract should it fall into the wrong hands.
Encrypted data is secured data.
As far as HIPAA is concerned, secured PHI is not subject to the Breach Notification Rule or the regulation’s stiff civil penalties.
HIPAA Compliance Checklist FAQ
Below, we answer a few common questions around HIPAA compliance.
What Are the Three Key Elements of HIPAA?
HIPAA is broken down into three rules—Security, Privacy, and Breach Notification. All rules apply to both covered entities and business associates.
Security Rule outlines safeguards to protect the confidentiality, integrity, and availability of electronic protected health information (ePHI).
Privacy Rule sets national standards to safeguard individuals’ medical records and other PHI, and establishes when PHI may be used and disclosed.
Breach Notification Rule requires that a breach of unsecured PHI is communicated to affected individuals, the HHS, and in some cases, the media.
Why Do You Need a HIPAA Compliance Checklist?
HIPAA is complex. Compliance will look different within different organizations depending on the nature of the company, its size, and exactly how PHI and ePHI is handled.
A HIPAA compliance checklist is a valuable resource that can help set you off on the right foot as you begin your compliance journey.
How Do You Verify HIPAA Compliance?
There is no certification for HIPAA compliance. However, the Security Rule requires companies to perform periodic evaluations to ensure policies and procedures meet the rule’s requirements. These evaluations can be done internally or by an outside organization.
While it’s not required, it’s a good idea to hire a third-party auditor to evaluate your policies and procedures to ensure you’re compliant with the law. Drata has a number of service partners with specific HIPAA compliance experience to consider as you search for a third-party auditor.
How Drata Can Automate Your HIPAA Compliance Program
Achieving HIPAA compliance can seem daunting. By introducing better security controls and mitigating your HIPAA-related risks, following this HIPAA compliance checklist will improve your overall security posture.
HIPAA has much in common with security frameworks, such as SOC 2 and ISO 27001, that you may already follow. Drata’s automated monitoring platform lets you manage your compliance programs at scale while keeping your data private and secure. We use our own platform to manage Drata’s HIPAA compliance.
Book a demo with our compliance experts to see how Drata can streamline your HIPAA compliance program.
See Third-Party Risk Trends
Get the 2023 Risk Trends Report to learn trends and pressing issues surrounding third-party risk and processes to manage it.