Understanding the NIST Incident Response Guide (Updated for 2025)
Learn about NIST’s 2025 updates to its incident response recommendations and prepare your company for an effective response to cybersecurity events.
A recent survey by PwC found that only 2% of executives have implemented cyber resilience practices across their entire organization. If your company is in the other 98%, what will happen if a bad actor strikes?
Forrester estimates cybercrime will cost $12 trillion in 2025, and you don’t want to become part of that statistic. However, dealing with security incidents is inevitable for most organizations. When an attack comes, having a plan in place instead of muddling through could save you millions of dollars and spare you from days (or even weeks) of downtime.
Attacks can come from many points and take many forms, so planning for every possibility is prohibitive. Prepare the smart way: with a security framework that gives your organization tools to respond to any attack.
NIST’s Incident Response Recommendations and Considerations guide, also known as Special Publication (SP) 800-61, lays out the outcomes companies should prioritize when they experience adverse events. Here’s everything you should know about the NIST incident response framework and why it’s important.
What is NIST Incident Response?
The National Institute of Standards and Technology (NIST) regularly releases cybersecurity guidance for federal agencies and private companies. Its Incident Response Recommendations and Considerations for Cybersecurity Risk Management publication is meant to help organizations reduce their risk of cybersecurity incidents and respond effectively to attacks.
Understanding the Updates in NIST 800-61 Revision 3 (2025)
In April 2025, NIST published revision 3 of SP 800-61. This new version builds off the NIST Cybersecurity Framework (CSF) 2.0 to provide a new Community Profile for cyber incident risk management. The Community Profile was built to address goals and practices that many organizations can use to improve their security posture.
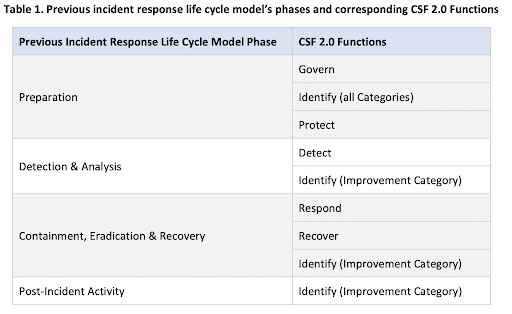
The previous NIST incident response guidance included a four-phase incident response life cycle and considered incident response a discrete set of responsibilities bounded by the few days surrounding an incident. Because security breaches are now more frequent and many take longer to recover from, NIST’s new guidance treats incident response as part of an organization’s cybersecurity risk management.
Effectively, this means NIST recommends you integrate your incident response planning into wider operations and react to and learn from incidents as they unfold. The new Community Profile assumes incident response activities will be continuous, as companies will learn and improve even when they’re not actively experiencing adverse events.
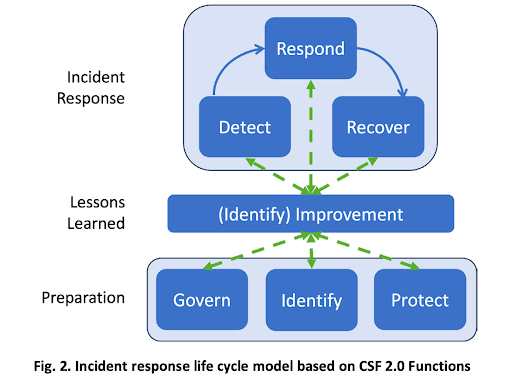
The 6 Categories of the New NIST Incident Response Model
NIST’s updated incident management and response model is organized into six categories, grouped by their relationship to an incident. The preparation phase includes the Govern, Identify, and Protect categories; the incident response phase includes the Detect, Respond, and Recover categories. NIST also puts the Identify category into its own Improvement category to emphasize the importance of continuous learning.
Within each category, NIST lists a number of outcomes of varying importance to your incident response process. While each company should determine its own preferred outcomes based on its size, industry, and the cybersecurity threats it faces, NIST’s Community Profile is an excellent starting point. We’ve summarized the items NIST designates as medium and high importance below.
Govern (GV)
The government category of the CSF Risk Management Framework guides organizations through establishing a risk management strategy and policy. To meet its requirements, your company must have a recorded cybersecurity policy, communicate rules and expectations, and enforce them.
An effective cybersecurity policy includes security practices required by laws, regulations, or contracts. It includes guidelines on documenting and categorizing cybersecurity risks. It also instructs employees on how to prioritize and respond to events given the services and outcomes others expect from your company. (For example, a cloud storage company needs to protect server uptime and data security, so events that threaten those functions are top priority. After a crisis, these foundational capabilities should be restored as soon as safely possible).
Once you’ve documented your policy and shared it internally as you would other important information, make sure your organizational culture lends itself to following it. If your organization hasn’t determined who owns essential cybersecurity functions, revisit your IT-related job duties so people know who to turn to during an incident. Managers should also be aware of the cybersecurity functions assigned to employees under them so they can provide support, ensure accountability, and assess performance.
Cybersecurity risks can also come through third parties. Make sure the vendors in your supply chain are aware of your cybersecurity policies and update contracts to require their compliance. Then, establish points of contact for any incident—on your end and theirs—so you’re not scrambling for information when a crisis hits.
The most effective cybersecurity planning is rolled into a larger organizational risk management process because a risk to your systems is a risk to your products or services. Buy-in from the highest levels helps promote a risk-aware workforce and a culture of continuous improvement. However, even cybersecurity teams or individuals who don’t have support from above can (and should!) regularly review their risk management strategy and adjust it if necessary to achieve their desired outcomes.
Identify (ID)
Identification refers to understanding the cybersecurity risks an organization faces. This awareness should come from multiple sources: Security forums, industry communities, and your vendors can all provide important information on the threats you’re likely to encounter.
With this cyber threat intelligence (CTI) in hand, you can start to assess risks and vulnerabilities within your organization’s systems. Inventory and map out your systems—hardware, software, services, network connections, data, and data flows—so you can better analyze them. Then, it’s time for threat modeling to help you understand attack vectors and surfaces and how bad actors might travel through your systems.
After you’ve modeled threats, think about how you’ll prioritize your responses to each risk facing your company. Note that risk response is not the same as incident response; this is the work you’ll do continually to prevent data breaches from occurring in the first place. There are four types of risk response:
Accept the risk without taking measures to mitigate or eliminate it.
Reduce risk through patching vulnerabilities where possible or adding security measures to protect against likely threats.
Partner with another party to share the risk, thus reducing the portion of it your company holds.
Eliminate the attack surface altogether.
Assess each risk individually to determine the best response.
Another large part of the Identify category is creating and disseminating multiple cybersecurity plans. Your organization should have clear written documents outlining your:
Vulnerability management plans: How you’ll assess vulnerabilities and test possible responses to them.
Risk response procedures: Your criteria for assessing and prioritizing risks.
Incident response plans: The steps your stakeholders should take when an incident occurs.
Business continuity plans: How your operations will continue when critical systems are under attack or unavailable.
Once your plans are in place, assess and improve them through tests and exercises. You’ll also want to revisit them after an incident once your team has reviewed what worked and where your organization’s response could have been better.
Protect (PR)
The Protect category is all about your organization’s processes to manage risks and protect its systems. There are two main types of protective measures: those that defend your physical systems and those that govern system access.
To keep your systems safe, actively manage your hardware, software, and services. Your company should restrict configuration management to IT and prevent others from installing software without authorization. IT must regularly update software and hardware and take your organization’s risk management guidance into account when choosing new tools.
Essential and/or sensitive hardware should be protected from physical threats. Environmental hazards may be a concern depending on where your servers or other key systems live. And, of course, physical access should be limited to essential personnel only.
Effectively governing system access requires you to address potential threats on two levels. The first is your security architecture: Systems should be designed and configured to protect data via information segmentation and regular re-authorization requests. A good security architecture can guarantee that even if a bad actor gains credentials to your system, the data they can access will be limited.
Access management also includes your organization’s practices for authenticating users and connections. All of your systems should be locked to authorized users, and individuals should only have access to tools and data they need. Manage your credentialing internally for maximum visibility and control over the process.
Finally, ensure your employees receive cybersecurity training and participate in exercises to help reinforce risk-aware practices. Everyone should receive a base level of training, but you may want to go deeper with individuals in specialized roles or those who have access to privileged information or systems.
Detect (DE)
The first category in the incident response grouping of NIST’s response framework is Detect. The functions under this umbrella are related to monitoring your systems, spotting anomalies, and understanding the potential scope of each incident.
Identifying potential incidents early allows your company to address them before they spread throughout your systems. The best way to catch potential problems is with continuous monitoring of your:
Networks and network services.
Computing hardware.
Software and apps.
Runtime environments.
Physical environment access logs.
Employee activity and usage patterns.
Connections with external services.
Communication and data flows.
Typically, companies invest in a security information and event management (SIEM) or security orchestration, automation, and response (SOAR) tool that consolidates and analyzes system activity.
These tools send alerts for events of low or no concern. Set up a system to analyze and rate potential incidents. Most SIEM and SOAR tools automatically filter events, alerting your team members only when human involvement is necessary.
Team members who receive an alert should have access to data and logs that help them analyze and scope the potential blast radius of an event. The documentation your company did in the preparation stages will help employees determine when an event rises to the threshold of an incident.
Respond (RS)
Once an incident has been declared, put your response plans into action. The goal of response is to contain and eliminate an incident. To do so effectively, teams need to use their judgment in concert with the company’s recorded risk evaluation criteria. It’s unlikely your entire incident response team will be called in at the first sign of something amiss, but as the incident progresses and responders gather more information, they might need to escalate issues.
The first step of incident response involves validating reports and then projecting the potential severity and urgency of the situation. The severity will depend on where your systems have been compromised, how many functions are or could be affected, and whether any sensitive data or information is at risk.
Once you know the basics of the situation, implement the relevant sections of your incident response plan. Because most incidents consist of multiple concurrent events, your team will need to prioritize response efforts. First, contain the incident: stop it from spreading further throughout your systems. An uncontained incident will take more resources to respond to and may overwhelm your team.
After containment, your teams can start mitigating the incident’s effects. While working through the Identify category, your department should have created business continuity plans, and now they come into play. At the same time, your eradication efforts should determine whether the incident has any persistence or the potential to recur due to a remaining vulnerability. Rooting out remnants of the threat and locking down affected systems against repeat attacks is a must before moving on to your recovery efforts—otherwise, you risk the same thing happening again.
While most of your team will be engaged with highly technical response work, it’s also important to have someone on the ground handling communications. Stakeholders, external partners, and customers should all receive information relevant to them that lays out what’s happening and where your response efforts are. The level of detail will vary as appropriate to different parties, but make sure you meet any laws or regulations governing incident notifications.
Recover (RC)
The Recover category covers steps your company should take after the incident has been eradicated and no threat remains. Like the response portion of your plan, recovery actions should be selected and prioritized based on the most complete information available to your team.
Some organizations may need to restore services in a certain order to ensure no further errors occur; others may prioritize based on access to and operation of essential functions. You may also find yourself working with third parties to determine the best order of operations. As during the response phase, it’s important to have open lines of communication with internal and external stakeholders.
When restoring data and systems from backups, all assets should be verified first to prevent the reintroduction of incident persistence. Once your efforts have been completed and normal operations restored, your company can declare an end to the incident and communicate this update to stakeholders and the general public.
Then, it’s time to review the incident and your team’s response. Companies with strong cybersecurity practices use the post-incident period to learn from what happened and strengthen their systems and response plans.
Directly after the incident has been eradicated, gather data and metadata that shows what happened and when from system logs and your SIEM or SOAR solution. Make a record of every action responders took during the incident. Teams should also discuss their experiences and share where they felt your organization’s plans were sufficient and where they were lacking. Put this information into an incident report that lays out your response and recovery efforts and what you learned from them.
You should also open an investigation into the incident. This may take longer to complete, as it’s not always clear which vulnerabilities were exploited and which threat actors were involved. However, the final report should outline the incident’s timeline and progression and which data or systems were involved. It should identify the root causes and incorporate community information regarding similar incidents or attackers.
Between the two reports, your company has what it needs to return to the preparation phase with a new outlook. It may be time to update your risk assessment and response to incorporate new context learned from your reconstruction of what happened. You’ll also want to revisit incident response and business continuity plans to resolve any issues your team found while executing them. These practices will help you handle future incidents more effectively.
NIST Recommendations for Incident Response Teams
The most important factor in any incident response effort is speed. From detecting anomalies quickly to alerting the right people to verifying incidents and beginning containment, the less time you take at each step, the better off your organization will be. A faster response can cut down on losses due to disruption of services and theft of sensitive information.
The second concept NIST emphasizes in its new incident response guidance is continuous improvement. Threatening actors are constantly improving their techniques, and your company must evolve its response practices to keep up with them. Test your response procedures to uncover gaps: People often don’t receive the information they need or have the resources necessary to take the most efficient and effective actions. Regularly updating your incident response capabilities and plans as you learn will help your company’s next response be quicker and smoother.
Finally, NIST emphasizes the importance of documentation. Organizations with strong cybersecurity practices write up their plans and procedures to avoid uncertainty or delays in their response activities. Some organizations create playbooks that lay out the steps individuals should take to respond to certain situations or threat types. Even if you don’t go into this much depth, record your criteria for assessing and categorizing vulnerabilities, risks, and incidents. This information is a must to help teams prioritize and respond to adverse events.
Be Incident-Ready With NIST CSF Compliance
NIST’s new incident response recommendations are built on its cybersecurity framework (CSF). That means organizations with internal transparency regarding their security posture and risk mitigation according to CSF controls will find it easy to build a compliant incident response plan.
Drata’s NIST CSF framework brings everything you need to monitor your tech stack into one place. We also centralize controls and documentation. This makes it easy for companies to see the gaps in their security posture and implement new controls. You can customize our NIST CSF framework to meet your business’s needs and speak with our solution architects and compliance advisors whenever you need.
Don’t let a cybersecurity incident catch you off guard. Book a demo to explore our NIST CSF solution today.
NIST Incident Response Guide Frequently Asked Questions (FAQs)
Still have questions about the NIST Incident Response Guide? We answer common queries below.
What are the Phases of NIST Incident Response?
NIST’s updated incident response framework splits the necessary steps into two phases: preparation and response. The preparation phase includes the Govern, Identify, and Protect categories, while the response phase includes the Detect, Respond, and Recover categories.
What are the Updates in Revision 3 of the NIST Incident Response Guide?
Revision 3 of NIST SP 800-61 treats incident response as an ongoing practice that is embedded into an organization’s wider cybersecurity program. It emphasizes continuous learning and development rather than assuming incident response activities only need to happen when an adverse event occurs.
Who Uses the NIST Incident Response Framework?
The NIST incident response framework is used by federal organizations and many in the private sector as well. The guidance contained in it can help any company create a strong and effective incident response plan.
Is NIST Incident Response Mandatory?
No. Compliance with NIST CSF is mandatory for federal agencies and organizations within their supply chain. NIST’s incident response guidance uses the same language as, but is separate from, CSF. However, it can help federal, federal-adjacent, and private businesses improve their cybersecurity practices and comply with other regulations like HIPAA and GDPR.