User Access Reviews: A Step-by-Step Guide, Best Practices + Checklist
Keep your organization’s data safe. Follow our step-by-step guide to streamline user access reviews and prevent security breaches.
On November 11, 2021, an employee at South Georgia Medical Center clocked out for the last time. The next day, they used their still-active credentials to download patient data onto a USB drive, triggering a HIPAA breach, felony charges, and a security nightmare for the hospital. Over 40,000 patients were affected.
This is an all too familiar mess, and it’s not limited to the healthcare industry. According to Verizon's 2022 Data Breach Investigations Report, 82% of data breaches were caused by credential theft, phishing attacks, and employee misuse or mistakes.
The uncomfortable truth is that countless data breaches stem from failing to manage who has access to what within your organization. The risks are everywhere, from former employees who still retain system access to current employees with excessive permissions and contractors whose temporary access never gets revoked.
The fix starts with user access reviews (UARs). In this article, we cover what access reviews are, why they matter, and how to run them effectively. We’ll also give you a checklist to streamline the process and protect your business from a common cause of data breaches: too much trust in the wrong hands.
What Are User Access Reviews?
A user access review is the process of checking who has access to your organization’s systems, what they can do with it, and whether that access is still needed. It helps you spot and remove unnecessary or risky permissions before they become a problem.
User access reviews answer four questions:
Who is accessing what systems and data?
What level of access do these users have?
Do these users have valid reasons for their access rights?
What updates need to be made to their access permissions?
A "user" in this context extends to anyone who interacts with your systems and data, each with different access needs:
Employees include full-time, part-time, and temporary staff who need access to company resources to perform their job functions. It covers everyone from entry-level workers to executives.
Business partners often need user access rights to collaborate on joint projects or shared platforms. Their access should be strictly limited to the systems or data necessary for the partnership, with formal agreements outlining how data is shared and how long access will be granted.
Vendors, such as IT or cloud service providers, require access to keep your systems running smoothly. However, their access should be restricted to only the systems they need and monitored closely for any unusual activity.
Contractors require temporary access to systems and data to complete their tasks, but only for a limited time. You want to grant them just enough access to do their jobs and revoke it as soon as their contract ends.
Former employees represent one of the biggest insider threats when their access hasn't been properly revoked. Companies that fail to withdraw access immediately after employees leave create significant security vulnerabilities.
Types of User Access Reviews
Organizations typically implement three types of access reviews:
Periodic access reviews: Scheduled at regular intervals (e.g., quarterly or annually), periodic reviews give you a broad view of who has access and whether that access still makes sense. They’re ideal for catching privilege creep and outdated access across the organization.
Event-driven access reviews: Happen in response to specific changes: someone joins, changes roles, switches departments, or leaves the company.
Continuous access reviews: Powered by automation, continuous reviews happen in real-time. Instead of waiting for a scheduled review, systems track changes to access, flag unusual behavior, and alert you to risks as they happen. They're best for high-risk environments, privileged accounts, and fast-scaling teams.
Why are Access Reviews Important?
User access reviews are one of the simplest, most effective ways to reduce security risks. Let’s examine how they benefit your organization.
They Protect Sensitive Data
The most obvious yet arguably most important benefit is preventing unauthorized access to your sensitive data and assets. Access reviews reduce your attack surface and limit the potential damage from both insider threats and compromised credentials.
They Prevent Common Access Issues
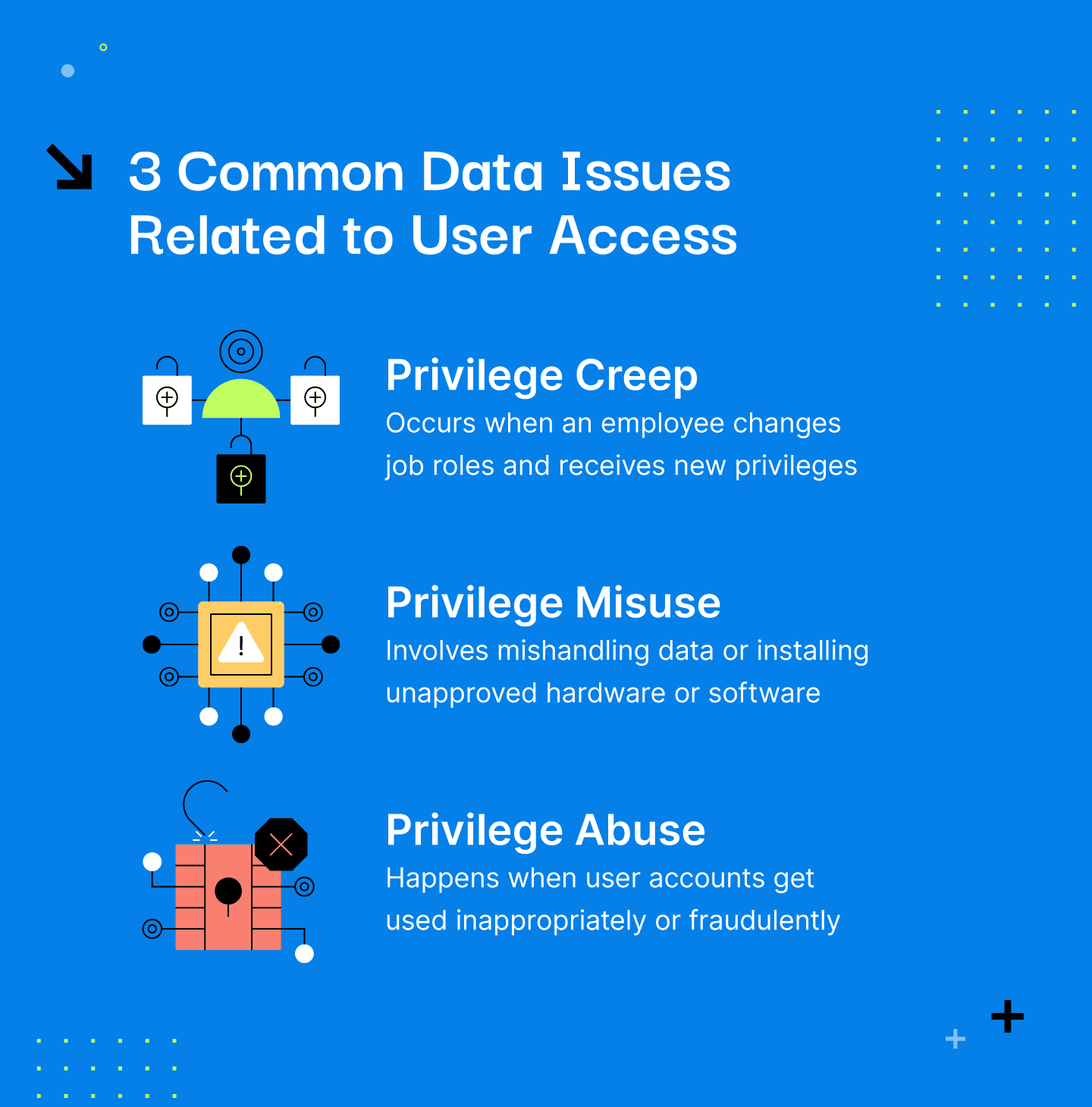
If you don’t conduct regular reviews, access problems build up quietly. Over time, they create serious risks:
Privilege creep occurs when an employee changes job roles within an organization and receives new privileges. It can happen naturally over time, where employees who have been with the organization a long time obtain access to more and more systems.
Privilege misuse involves mishandling data or installing unapproved hardware or software.
Privilege abuse happens when user accounts get used inappropriately or fraudulently—either maliciously, accidentally, or through willful ignorance of policies.
Many data breaches trace back to access that was never revoked or reviewed. Access reviews are how you catch these issues before they escalate.
They Help You Meet Compliance Requirements
Many standards, laws, and regulations include guidance for companies to implement user access measures within their organization. Strict regulatory standards govern many industries (think Europe's GDPR for data protection, HIPAA for healthcare, or PCI DSS for payment card information).
Auditors want to see proof, and that includes documented access reviews, evidence of changes made, and ownership over who’s responsible for access decisions. If you fail to review access regularly, you could potentially face audit exceptions, fines, and loss of certifications.
They Reduce Software Costs
Many platforms charge by user, role, or access level. If your systems are full of dormant accounts or over-provisioned users, you’re likely overpaying. Access reviews help you:
Identify unused or inactive accounts still tied to paid licenses.
Spot roles with elevated permissions that trigger higher subscription tiers.
Trim unnecessary access in third-party SaaS tools and internal systems.
As your company scales, license sprawl can turn into a silent cost center. Regular reviews give your IT and finance departments visibility into what’s actually being used, so they can right-size spend without disrupting teams.
What Standards, Laws, and Regulations Encourage User Access Reviews?
User access reviews are built into nearly every major compliance framework. We dig into a few common ones and how they handle user access reviews below, but you can also find a general overview in the following table:
Framework | User Access Review Requirement |
Control 6 establishes requirements for ongoing assessment and adjustment of user permissions to match current organizational roles. | |
CJIS | Policy 5.5.1 establishes requirements for the evaluation of user permissions within law enforcement information systems. |
AC.L2-3.01.05 establishes requirements for the evaluation of user permissions to maintain minimal necessary access. | |
Calls for the evaluation of user permissions to ensure access aligns with specific operational requirements. | |
FTC Safeguards Rule | Requires financial organizations to consistently evaluate employee access to customer data based on operational necessity. |
Article 25 establishes data protection requirements that include limitation and evaluation of personal data access. | |
CCPA/CPRA | Section 1798.100 establishes security requirements, including controls over personal information access. |
Administrative safeguards under §164.308 require periodic management of workforce access to protected health information (PHI). | |
Control A.5.18 establishes requirements for the evaluation and adjustment of user permissions based on current responsibilities. | |
The Identity and Access Control function requires management and evaluation of user permissions for risk mitigation. | |
Control AC-02(j) establishes requirements for the evaluation of user accounts for compliance verification. | |
Builds on NIST 800-53 AC-02(j) with specific timing: monthly evaluation for privileged accounts, semi-annual for standard accounts. | |
TX-RAMP | Implements NIST 800-53 AC-02(j) with minimum annual evaluation requirements for user access assessments. |
NYDFS NYCRR 500 | Section 500.7 establishes requirements for limitation and evaluation of access to sensitive financial information. |
Requirement 8.1.6 establishes semi-annual evaluation requirements for user accounts and associated permissions. | |
SOC 1 | Requires access management and evaluation processes for financial reporting system security. |
Control CC6.2 establishes requirements for the management of user credentials throughout the employment lifecycle. | |
SOX | Section 404 establishes internal control requirements for financial integrity, including periodic access evaluation. |
Payment Card Industry Data Security Standard (PCI DSS)
PCI DSS is a data security standard that ensures companies accept, process, store, or transmit cardholder data safely and securely. PCI DSS transitioned from the current version v3.2.1 to v4.0, effective March 31, 2025.
Requirement 7, Restrict Access to System Components and Cardholder Data by Business Need to Know, states that “to ensure critical data can only be accessed by authorized personnel, systems and processes must be in place to limit access based on need to know and according to job responsibilities.” Organizations are required to:
7.1 Define processes and mechanisms for restricting access to system components and cardholder data by business need to know.
7.2 Define and assign access to system components and data.
7.3 Manage access to system components and data via an access control system.
Requirement 8, Identify Users and Authenticate Access to System Components, also states that “two fundamental principles of identifying and authenticating users are to 1) establish the identity of an individual or process on a computer system, and 2) prove or verify the user associated with the identity is who the user claims to be.” To this end, organizations must:
8.1: Define processes for identifying users and authenticating access to system components.
8.2 Strictly manage user identification and related accounts for users and administrators throughout an account’s lifecycle.
8.3 Establish and manage strong authentication for users and administrators.
8.4 Implement multi-factor authentication (MFA) to secure access to the common data environment (CDE).
8.5 Configure multi-factor authentication (MFA) to prevent misuse.
8.6 Strictly manage the use of application and system accounts and associated authentication factors.
SOC 2
SOC 2 is a security framework that guides how companies should manage, process, and store customer data based on the Trust Services Criteria (TSC). SOC 2 audits evaluate the effectiveness of your organization's security controls, with access management being a core component.
CC6 is the control series relevant to logical and physical access. It's broken down into eight specific requirements, but the most relevant to access reviews is CC6.2, which states that you have to register and authorize new users, and modify or remove access promptly when job responsibilities or employment status changes.
What this means in practice:
Employee offboarding management: Implementing automated access restrictions when an employee leaves to ensure departures don’t turn into security breaches.
Physical access controls: Access control isn’t limited to the digital world. Physical access points (security gates, door locks, employee ID cards) also need to be managed.
Multi-factor authentication (MFA): MFA is a common control that helps companies secure logins and prevent unnecessary access sharing.
Health Insurance Portability and Accountability Act (HIPAA)
The Health Insurance Portability and Accountability Act—better known as HIPAA—is the United States’ legal standard for protected health information (PHI) protection. The HIPAA Security Rule outlines requirements (45 CFR § 164.308) for managing access to PHI and electronic protected health information (e-PHI), which includes:
Information access management: Covered entities must implement policies and procedures for authorizing role-based access to e-PHI.
Workstation and device security: Covered entities must implement policies and procedures outlining the proper use of and access to workstations and electronic media.
Audit controls: Covered entities must implement hardware, software, or procedural mechanisms to record and examine access and other activity in information systems that contain or use e-PHI.
General Data Protection Regulation (GDPR)
The European Union passed the General Data Protection Regulation (GDPR) in 2016, and it went into effect in 2018. GDPR aims to regulate how organizations collect, process, and store the personal data of EU residents. Article 32 of the regulation requires organizations to “implement appropriate technical and organizational measures to ensure a level of security appropriate to the risk,” which includes identity and access management (IAM).
Managing identity and access management under GDPR can include:
The Principle of Least Privilege (POLP): Providing the minimal level of permissions to a user to do their job.
Segregation of duties: An approach requiring more than one user to complete tasks related to the collection or processing of customer information.
Authentication: Techniques like two-factor authentication (2FA) or MFA can verify user identities.
Sarbanes-Oxley Act (SOX)
The Sarbanes-Oxley Act is a law passed by the U.S. Congress on July 30, 2002. Known as the SOX Act, it is meant to protect investors from fraudulent financial reporting by corporations. ITGCs or IT General Controls are a subset of the Sarbanes-Oxley (SOX) internal control set that protect the security of IT systems and data centers, data backup and storage, and change management activities.
The ITGS portion of the SOX Act also includes requirements for limiting access to and protecting financial data. Managing access rights under SOX includes:
Overseeing access rights when onboarding new employees, as employees transition to new roles, and when they leave the organization.
Implementing Segregation of Duties (SoD).
Maintaining an access control matrix.
Performing periodic access audits.
The User Access Review Process in 6 Steps
So, how exactly do you review user access? Below is an easy six-step process you can also access through our downloadable checklist.
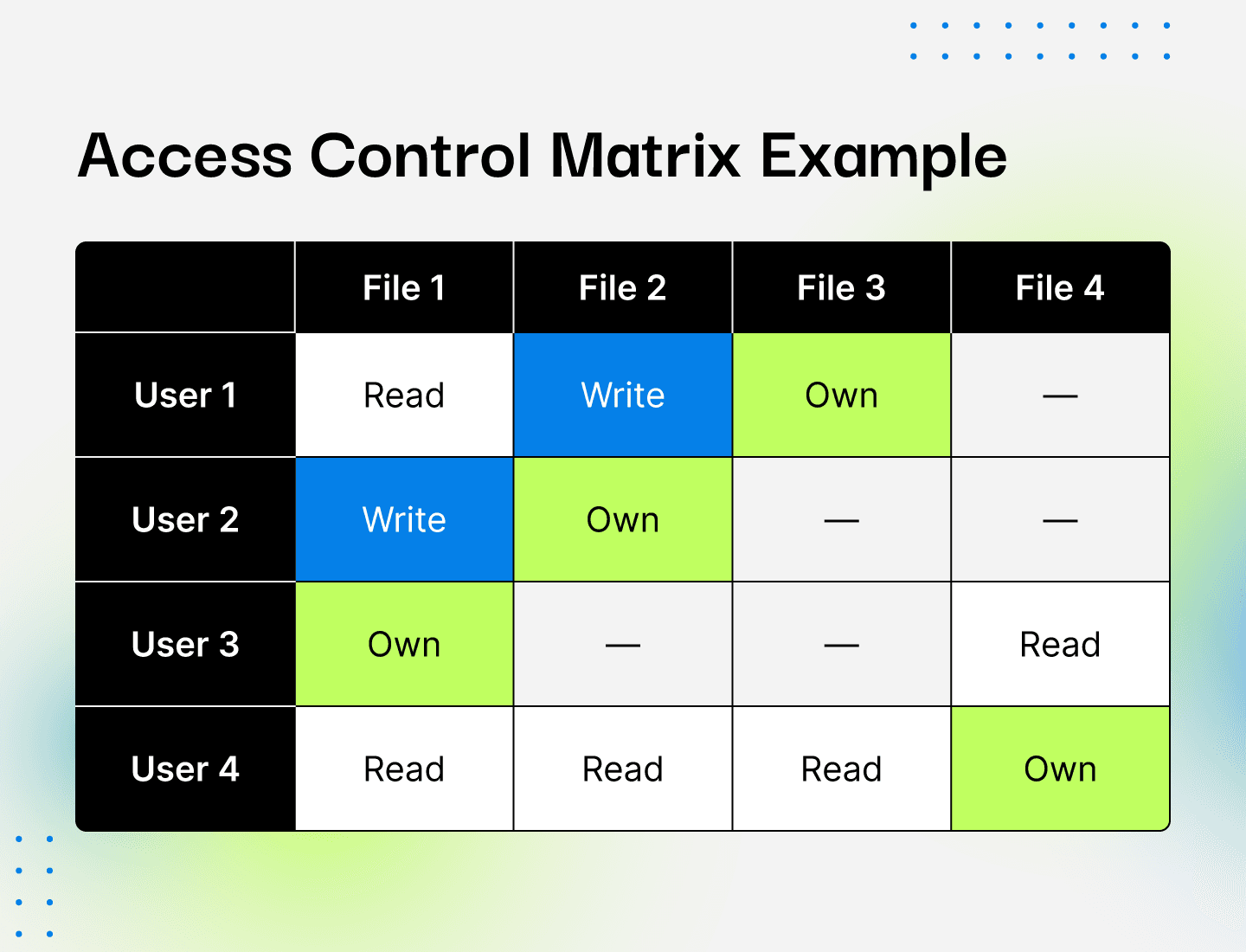
Step 1: Create an Access Control Matrix
The first step in locking down user access is to understand where your high-risk data lives and determine who needs access. One way to do this is by creating an access control matrix.
An access control matrix is a table that identifies access permissions between specific subjects and objects. A subject refers to the people who need access to objects. Objects are files, resources, system processes, data, or tools that subjects need to do their job.
First, you’ll need to compile a list of all users who have access to your systems, including employees, contractors, partners, vendors, and service providers. The list should also include the systems, applications, and data to which each user has access.
Then, designate user permissions for each subject and object within your organization. This includes specifying what they can do with the systems or data to which they have access. Companies often use the following attributes to assign varying levels of permissions:
Read: The subject can open and read the object, but not edit it.
Write: The subject can read the object and add or write new content.
Execute: The subject can execute particular programs.
This breakdown might feel like overkill, but it’s how you identify risk. Someone with read-only access to an internal dashboard is very different from someone with admin access to cloud infrastructure, yet both might show up in your user directory as “active.”
In cases where access is time-bound (say, for a short-term contractor), include expiration dates and document when those permissions should be removed. Inactive accounts or forgotten exceptions are common causes of data breaches.
If you're using identity providers like Okta, Azure AD, or AWS IAM, take advantage of built-in reporting to export user and access data directly. Better yet, automate the process entirely with a trust management platform that consolidates access logs across your stack.
Step 2: Develop an Access Management Policy
After establishing your access control matrix and understanding the current access permissions within your organization, you can draft your access management policy. This policy will serve as the foundation for how your organization handles user access moving forward.
Look at your systems and data. Which assets require the most protection? Which systems store sensitive or regulated information, like customer data, financial records, intellectual property, or healthcare information? Categorize these assets based on both sensitivity and business impact. A platform that holds PII may carry more regulatory weight, while an internal tool that supports daily operations may have greater business continuity implications.
Next, outline the roles within your organization and the permissions required for each. Cover every team and department, and define:
Who has the authority to grant or revoke access
Who is responsible for conducting access reviews
How these roles fit into your broader security strategy
Then, document standard processes. Establish how access is requested, how approvals are handled, and how long access should be granted. If you use controls like MFA, SSO, or PAM, explain how those are enforced and integrated. Be specific, as ambiguous guidance is hard to follow and harder to audit.
Finally, set review frequencies and triggers. Determine how often access should be reviewed based on your risk profile and compliance obligations. One access review myth is that regular user access reviews occur quarterly or monthly. However, best practices are to do access reviews every six months or once a year. High-risk systems may require more frequent reviews, while lower-risk systems may be reviewed less often. You should also define triggers that require immediate review, such as:
Employee terminations or role changes.
New regulatory requirements.
System changes or security incidents.
Step 3: Begin a User Access Review
With your access policy in place, you're ready to begin the review. This is where you compare current access against what users actually need and take action when something doesn’t align.
One thing to keep in mind is that a successful review involves multiple stakeholders. IT teams typically generate access reports and manage technical implementation, but they shouldn’t decide who needs access. That responsibility falls to department heads, team leads, and data owners—people who understand what access their teams need to do their jobs.
Begin the review by examining each user's access permissions in relation to their current role. The review is conducted based on two criteria:
Is the user’s access to the system or service appropriate based on their role?
Are the user’s permissions within the system or service appropriate based on their role?
For example, a support rep with admin access to your CRM might have needed it in a previous role but not anymore. Similarly, someone who transferred teams may still have access to systems they no longer use.
Then, flag unnecessary or risky accounts. Look for accounts that shouldn’t exist or that represent outsized risk. These might include:
Former employees or contractors who still have access.
Shared or generic accounts with unclear ownership.
Dormant accounts that haven’t been used in months.
Privileged accounts assigned to users who don’t need elevated access.
Vendor accounts that are no longer required.
Every account you flag should be documented along with the action needed, whether that’s revoking access, adjusting permissions, or investigating further.
Step 4: Train Team Members on the Importance of Access Permissions
Access controls don’t work if people don’t understand them. Your team should receive formal training on your access management policy to ensure they understand the importance of following those procedures.
Explain to your team why access controls matter. Paint the big picture—how improper access can lead to data breaches, security incidents, or compliance violations. To drive the point home and make the security risks feel more tangible, use real examples.
Highlight the consequences of non-compliance at the individual level. Make it clear that mismanaging access doesn’t just impact the company through fines, legal penalties, or reputational damage, but could also have a resounding impact on each individual team member dealing with the fallout of a breach.
However, don't leave it on a negative note. Shift the focus to success stories and share examples of how proper access controls have prevented these issues. If your company has averted a crisis thanks to well-managed access, that's a powerful tale to tell. If not, industry examples abound.
Each department or team will have different access needs, so tailor your training to fit those specific requirements. For example, IT teams might need a deeper understanding of system-level permissions, while other departments need to understand their role in and procedures for requesting, granting, and managing access. Make sure the training is relevant to each group’s day-to-day responsibilities.
Step 5: Implement Role-Based Access Control (RBAC) and the Principle of Least Privilege (POLP)
As you’re considering ways to further protect your data from unauthorized access, there are two effective techniques to consider: Role-Based Access Control (RBAC) and the Principle of Least Privilege (POLP).
With RBAC, you assign permissions to roles (like Sales Rep or DevOps Engineer) rather than individuals. Each user inherits the access they need based on their role. RBAC implementation starts with asking:
What systems does this role need to access?
What level of access is appropriate?
Should that access expire automatically (e.g., for temp roles or projects)?
Avoid creating overly granular roles. Start broad, refine as needed, and revisit role definitions during future reviews.
POLP means giving users only the access they need to do their job. It prevents over-permissioning, limits exposure, and contains potential damage from compromised accounts. You can put POLP into practice by:
Starting new users with minimal access, then adding if the occasion calls for it.
Reviewing access after role changes or project completions.
Limiting admin or elevated privileges to just those who require them.
Using temporary, time-bound access for contractors or short-term needs.
Step 6: Analyze Access Review Results and Improve Processes Continuously
Every review is an opportunity to spot trends, fix weak points, and improve over time.
Analyze the results to identify recurring trends or issues. Are there specific systems or departments that frequently have inappropriate access? Are certain permissions being granted too broadly? Recognizing patterns helps you understand where your access controls may be weak or misaligned.
Also, consider what slowed you down. What confused stakeholders? Where did things fall through the cracks? Common friction points include:
Poor visibility into user access across systems.
Delays in getting sign-off from business units.
Unclear or inconsistent approval workflows.
Gaps in documentation or follow-through.
You can then use the review results to improve both access controls and the process itself. That might mean:
Tightening default permissions for specific roles.
Automating revocation during offboarding.
Updating your policy to reflect new systems or review triggers.
Building automated alerts for dormant or high-risk accounts.
Fold what you’ve learned back into your policy, training, and tooling. That way, each review strengthens the foundation for the next, which makes access management smarter, faster, and more secure with every cycle.
Obstacles to Conducting User Access Reviews
In an ideal world, implementing cybersecurity measures would be as easy as flipping a switch. However, as relentless news about data breaches reminds us, security is anything but straightforward.
User access reviews aren't an exception. While essential for maintaining a strong security posture and staying compliant, they can pose a formidable challenge.
Scope and Complexity for Large Organizations
User access reviews can be a long process for organizations with complex IT infrastructures and hundreds (or thousands) of employees. Reviewing access rights for all these people across multiple systems and applications is detail-oriented work. Each system may have its own set of permissions and access levels, which only adds layers of complexity to the process.
Of course, business doesn't stop for these reviews. IT teams must conduct them without disrupting the daily flow of work and halting productivity.
Resistance from Stakeholders
Getting buy-in from all necessary stakeholders can be an uphill battle. Department heads might perceive access reviews as just another administrative task eating into their team's productivity. There's a common worry that tightening access might slow things down or make work more complicated.
It's not just the higher-ups who might push back, as individual users can get pretty attached to their access privileges. When permissions are revoked, you might hear grumbling—or worse, run into attempts to work around the new restrictions. If the reasoning behind access changes isn't clearly communicated, people can get frustrated and become uncooperative.
Lack of Clear Processes and Visibility
It's not unheard of for companies to lack a complete inventory of the systems and applications their employees can access. To make matters worse, different departments control access to different systems, turning what should be a straightforward review into a wild chase across the organization.
Then there's the challenge of managing user identities throughout their lifecycle, from onboarding to role changes to offboarding. Keeping track of appropriate access levels can easily slip through the cracks, resulting in access creep and a number of orphaned accounts.
User Access Review Best Practices
The obstacles might be plentiful, but they’re not insurmountable. Below, we outline a few best practices for keeping your access reviews efficient, thorough, and aligned with your organization's security and compliance needs.
Prioritize High-Risk Systems and Data
Where access risk is concerned, not all systems are equal. During access reviews, prioritize those that contain sensitive data, as they are often the primary targets for external threats and insider misuse.
High-risk systems generally include those that:
Store or process personally identifiable information (PII)
Contain financial data or transaction records
House intellectual property or trade secrets
Handle customer data or other confidential information
Are critical to your core business operations
Establish (and Stick to) a Consistent Review Schedule
A consistent schedule—whether every six months or annually—turns access reviews into a regular part of your security practices. You'll catch issues like privilege creep and unnecessary access early, and prevent them from slipping under your radar until they snowball into major security risks.
Consider your organization's operational calendar to create realistic schedules that your team can follow. Avoid scheduling comprehensive reviews during busy periods like end-of-quarter sales pushes, annual budget cycles, or holiday seasons when key stakeholders may be unavailable. Plan reviews for periods when both IT teams and department managers have bandwidth to participate meaningfully.
In some industries, regulatory requirements may dictate how frequently reviews need to occur, so align your schedule with any compliance obligations. Set up automated reminders and assign clear ownership for initiating reviews. Without accountability measures, even the best-intentioned schedules tend to slip when other priorities compete for attention.
You might also want to stagger reviews by system type or department rather than trying to review everything at the same time. This way, you spread the workload more evenly throughout the year and ensure that each review gets the attention it deserves.
Involve Department Heads in the Review Process
The IT team often spearheads access reviews, but it's important to involve department heads and managers who have a deeper understanding of what their teams need to be able to access.
Department heads can better determine whether their team's access is appropriate and can flag any unnecessary or outdated permissions. They understand the nuances of different roles within their departments and can identify when someone needs access for cross-functional projects or temporary assignments that might not be obvious from job titles alone.
Document Everything
If it's not written down, it didn't happen. It’s in your organization’s best interest to keep detailed records of who has access to what, any changes you make during reviews, and why you're granting or revoking access. In the event of a security incident or an audit, you’ll be able to demonstrate that your organization is following best practices for access management.
Documentation also helps keep things consistent from one review to the next and lets you easily spot how access has changed over time. Create standardized templates for recording review decisions, including the rationale behind each change and who approved it.
Also, track the entire review process, including who participated, what systems were reviewed, and any challenges or exceptions that came up. This will help you improve future reviews and maintain a paper trail when auditors come knocking.
Store all documentation in a centralized, secure location that authorized team members can easily access. Consider using your GRC platform or compliance management system to maintain these records alongside other security documentation.
Automate User Access Reviews Where Possible
Manually tracking access across your entire organization is both time-consuming and susceptible to human errors. There are parts of the process where you can leverage automation to save time and improve the accuracy and consistency of your reviews. Automation tools can:
Generate regular user access reports.
Send timely reminders to reviewers.
Flag unusual access patterns.
Track the progress of ongoing reviews.
While automation handles these routine tasks, your team can focus on the aspects that require human judgment, like evaluating unusual access patterns or making decisions about appropriate levels of access.
Integrate Access Reviews into Employee Lifecycle Management
Access reviews work best when they’re part of the employee lifecycle. When someone joins the company, their access should align with a predefined package for their role. If they need more, then require manager approval and document the reason.
As employees change roles, take the time to reassess. Review what they already have and remove anything that’s no longer relevant. When someone leaves, move quickly: confirm that all permissions are revoked, shared accounts are secured, and credentials are no longer active. It's one of the simplest ways to prevent avoidable security gaps.
Take the Busywork Out of Access Reviews
Manual access reviews are tedious, time-consuming, and error-prone. Drata takes the complexity out of the process by automatically pulling access data from your connected systems, organizing it by role, and mapping it to your compliance framework, so you can focus on the decisions that matter—not the busywork.
With Drata, you can:
Automate recurring user access reviews across your entire tech stack.
Assign reviews to the right stakeholders with clear, trackable workflows.
Get audit-ready evidence with every review cycle.
Access reviews don’t have to slow you down. With Drata, they just get done.
Schedule a demo with our team to learn more.
User Access Reviews Frequently Asked Questions (FAQs)
Below, we give you the answers to the most common questions about user access reviews.
What is the User Access Review Process?
The user access review process is a systematic evaluation of who has access to your organization's systems, apps, and data, and whether that access is still appropriate. The process involves six steps:
Creating an access control matrix to map current permissions
Developing or updating your access management policy
Conducting the actual review by comparing current access against user roles
Training team members on the importance of access management
Implementing role-based controls and least privilege principles
Analyzing results to improve your processes continuously
What is the Goal of a User Access Review?
The primary goal of user access reviews is to ensure that only authorized individuals have access to the systems and data they need to perform their current job functions. They help prevent data breaches by identifying and removing unnecessary access, addressing privilege creep where employees accumulate permissions over time, and ensuring that former employees or contractors no longer have active access to your systems.
User access reviews also support regulatory compliance by demonstrating that you have proper controls in place to protect sensitive information and maintain an audit trail of access decisions.
Is a User Access Review a Detective Control?
Yes, user access reviews are considered detective controls because they identify problems after they've occurred rather than preventing them from happening in the first place. Reviews detect issues like inactive accounts, excessive permissions, or inappropriate access that may have developed over time.
That said, access review programs also include preventive elements, such as role-based access controls and automated provisioning processes that reduce the likelihood of access problems occurring initially.
How Frequently Should You Conduct User Access Reviews?
Most organizations should conduct user access reviews annually or semi-annually, depending on their risk profile and regulatory requirements. High-risk systems and privileged accounts may require quarterly reviews, while lower-risk systems might be reviewed every 18-24 months.
Who Should Conduct User Access Reviews?
User access reviews require collaboration between multiple stakeholders. IT teams typically handle the technical aspects, such as generating access reports and implementing approved changes. Department managers and business owners evaluate whether access is appropriate for their team members' current roles and responsibilities.
HR teams provide information about employee status changes, while compliance or security teams ensure the review process meets regulatory requirements. Some organizations also involve external auditors to provide independent validation of their review processes and findings.