Third-Party Risk Management
Not a fan of risky business? Identify, evaluate, and monitor vendor risk with Drata’s all-in-one third-party risk management (TPRM) so you can be confident in the vendors you work with.
Not a fan of risky business? Identify, evaluate, and monitor vendor risk with Drata’s all-in-one third-party risk management (TPRM) so you can be confident in the vendors you work with.
With 83% of companies facing negative consequences from TPRM processes, it’s crucial to reduce blindspots, know who you’re doing business with, and improve how you manage risk.
Populate your vendor directory and keep it up to date to have a complete picture of your vendor ecosystem and the risks they pose to your organization so you can make informed decisions.
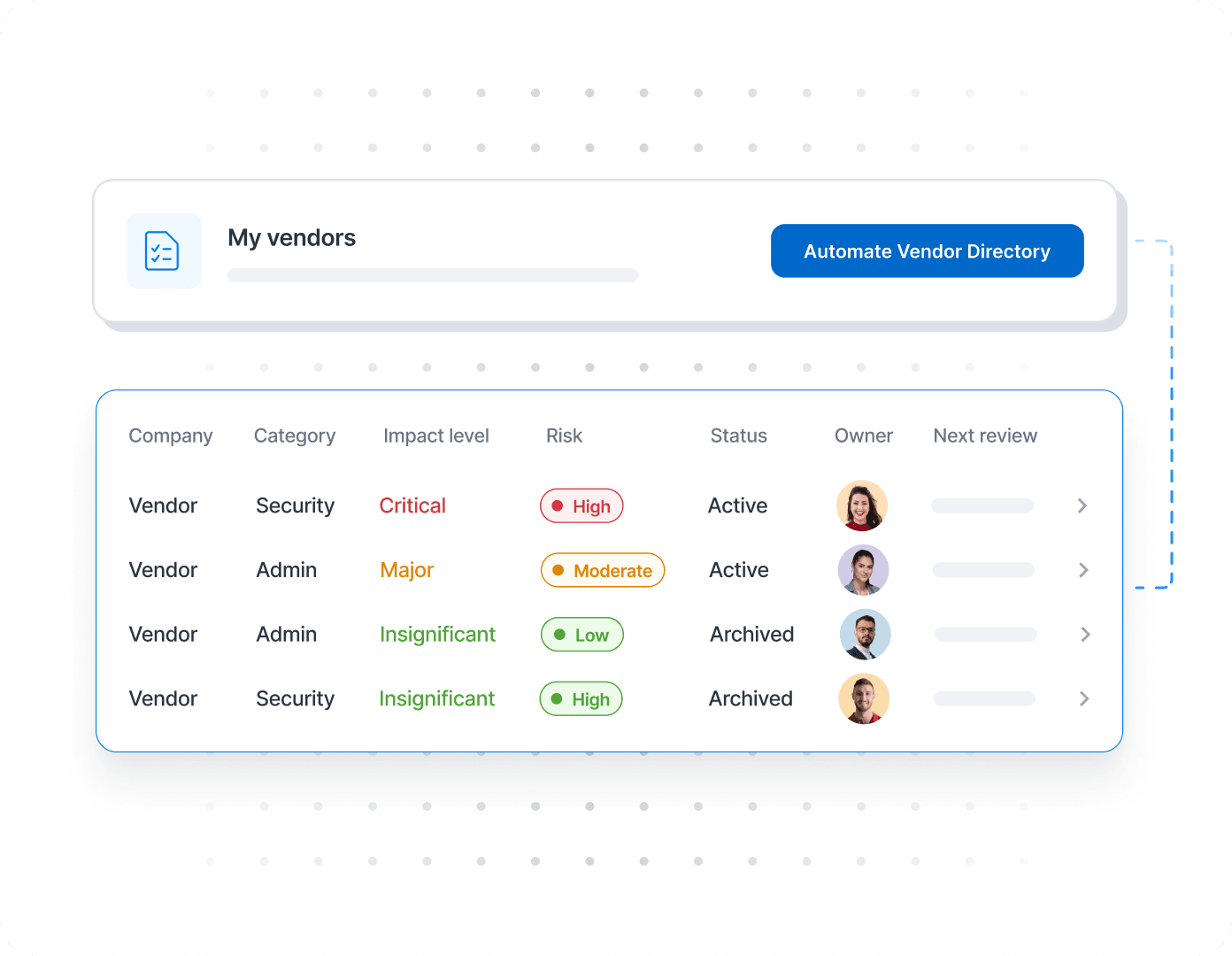
With all your vendor information in one place, you can streamline the risk management process and minimize human error.
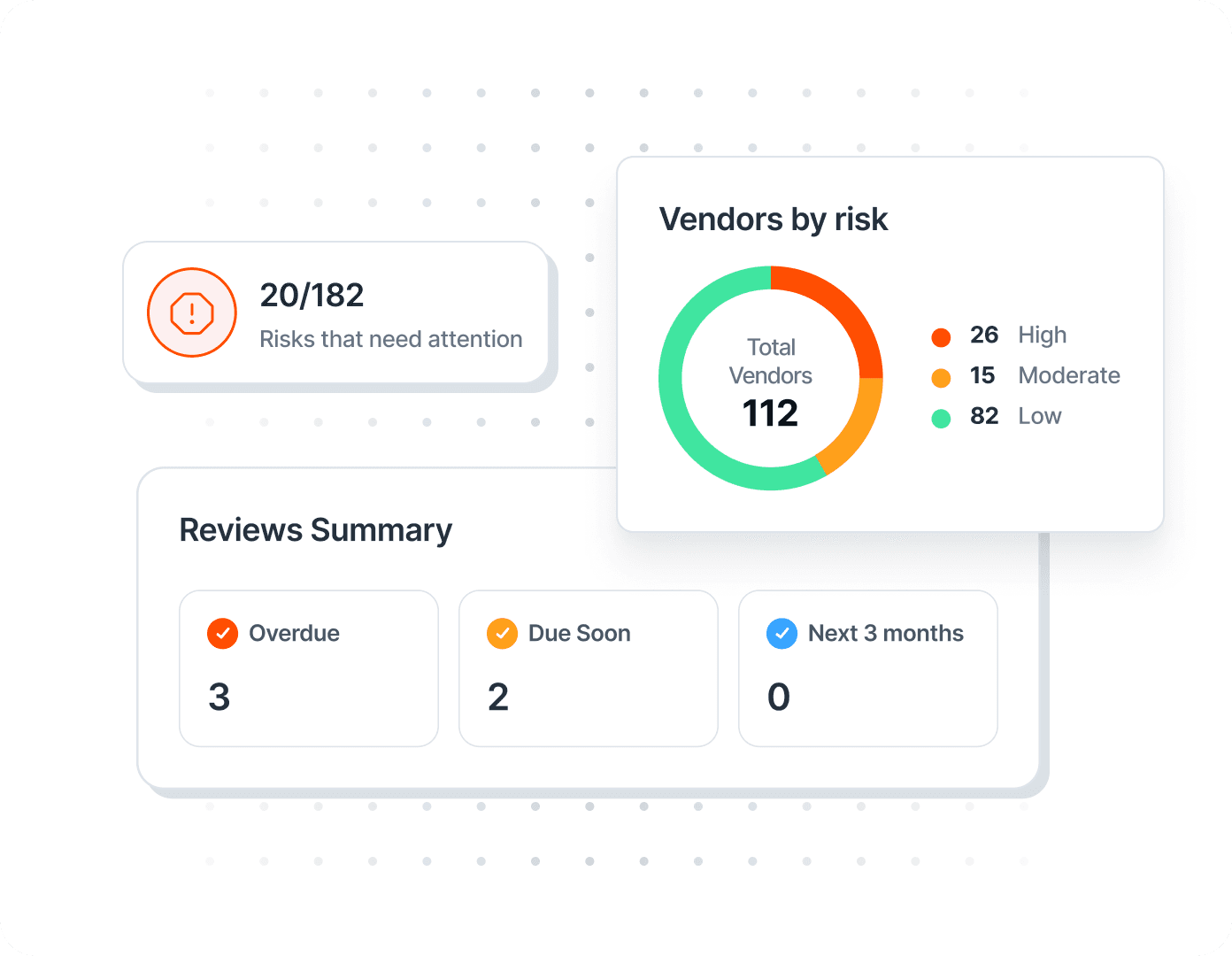
Automate the way you assess potential impacts of vendors, and easily identify your highest risk vendors. Identify and track Vendor Risks, including impact, likelihood, and treatment plan, as part of your organizational risk management program. Document and report vendor information to auditors without the hassle of managing multiple spreadsheets and tools.
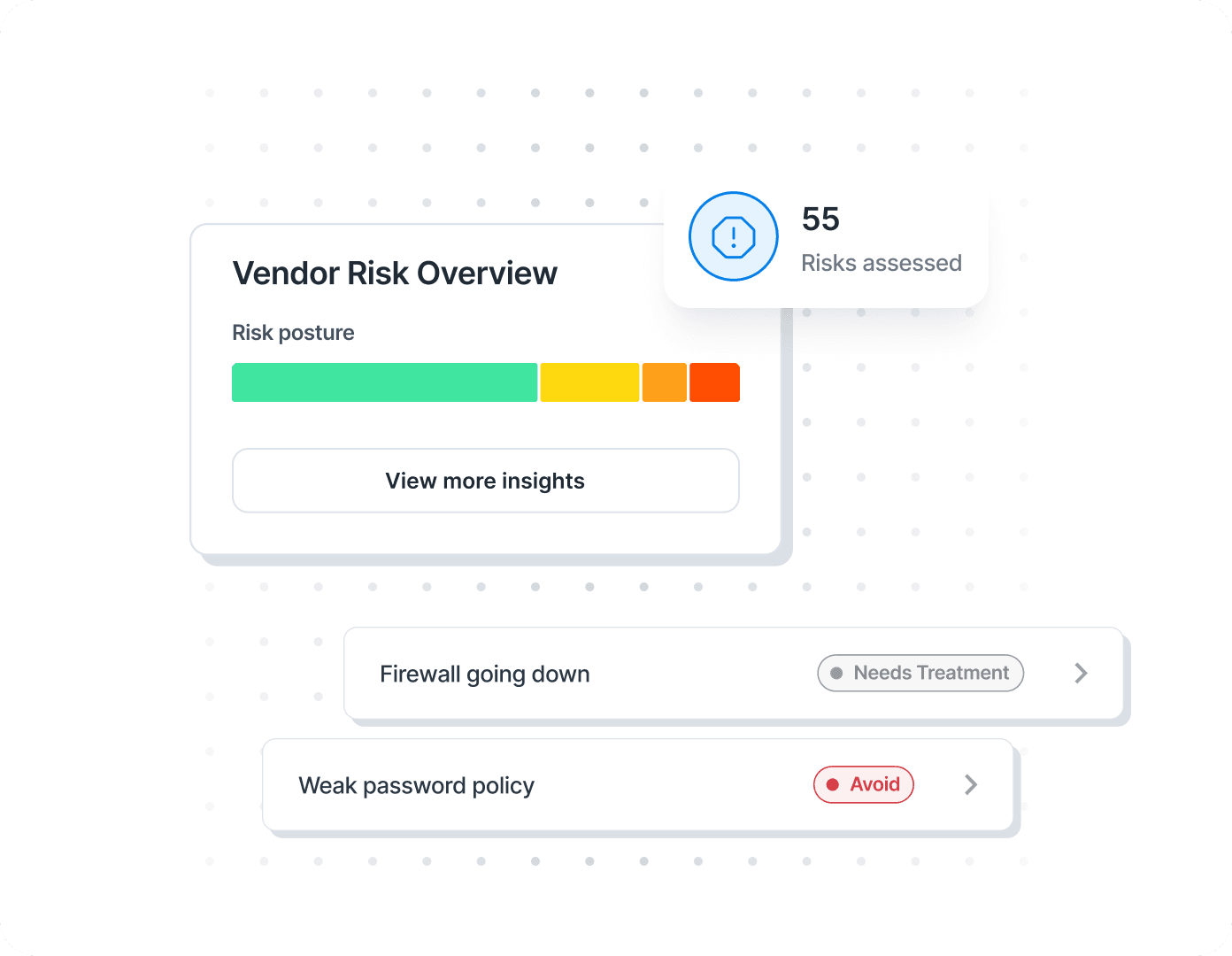
Risks don’t stop. So neither should your risk management. Proactively address vendor performance by conducting security reviews, sending custom security questionnaires based on vendor impact, and setting reminders for your next security review. With this proactive process, you can quickly spot and mitigate new security gaps before they become more significant issues.
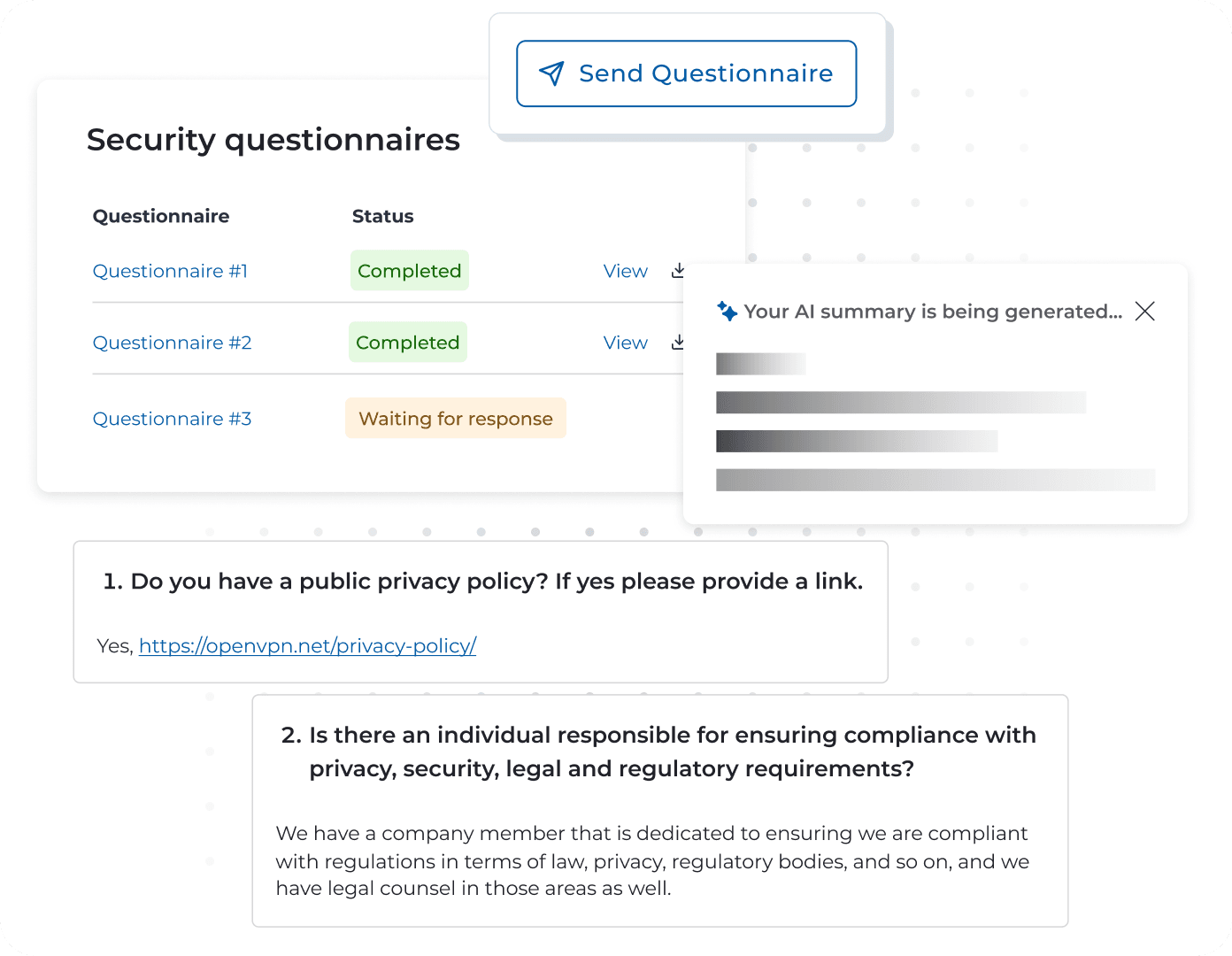
Risky business has met its match. Use Drata AI to summarize the vendor security questionnaire responses you’ve received—either inside or outside of Drata—to quickly determine whether vendors meet your teams’ security standards and identify potential risk. Then, easily share to communicate your findings with internal stakeholders.
Get the 2023 Risk Trends Report to learn trends and pressing issues surrounding third-party risk and processes to manage it.
Why Do Customers Trust Drata? Results.

Using Okta SSO, we populate your Vendor Directory so you have a single source of truth of your vendors' security information.

Bulk Upload quickly adds vendors to your Vendor Directory, while Bulk Update easily populates new info across multiple vendors.
Meet compliance requirements by documenting your vendors’ security reports, certifications, and share with auditors.
Standardize the way you assess vendor impact and analyze potential security threats with automated impact analysis.

Gain deeper insight into your vendors’ risk posture, then review questionnaire responses and take action on their responses.

Quickly understand security questionnaire responses to identify potential vendor risks, and share with internal stakeholders.

Monitor vendor risks and track them as part of your organization’s Risk Register.
Easily interpret and share the current state of your vendor risk management program to your C-suite.
Identify, evaluate, and monitor third-party risk with Drata.
Looking For More?
Check Out Our Latest Risk Resources
Frequently Asked Questions About Third Party Risk Management
What is third-party risk management?
Third-party risk management is the process of identifying and mitigating risks created when working with outside organizations. It is a proactive solution to risk control, which provides the framework, policies, and procedures you need to evaluate new and existing third-party partnerships.
How do I get started with building a third-party risk management program?
Here's a simple three-step TPRM process to ensure your company is mitigating third-party risk when possible:
Review and revise existing risk policies. Keep third-party exposure in mind. Be sure to consider how third parties can impact regulatory and other compliance requirements.
Conduct an audit of third-party relationships. Extend this review beyond your formal purchasing contracts. Consider open-source dependencies, workgroup-level relationships, and shadow IT. Understand the risks created by these relationships.
Draft internal and external TPRM policies. Supplement these policies with compliance expectations for specific business units.
What are the stages of third party risk management?
Evaluation: Assess a third party’s ability to manage and mitigate risk.
Onboarding: Obtain formal agreements with specific compliance expectations.
Monitoring: Evaluate third-party security and risk management systems regularly.
Maintenance: Update policies and respond to risks as they are identified.
Offboarding: Sever system integrations and destroy or return business records.
How do you mitigate vendor risk?
Vendor risk can be mitigated by having a third-party risk management program. An effective third-party risk management program reduces:
Cost: Organizations develop proactive measures to prevent or mitigate financial risks.
Compliance risks: A TPRM framework identifies legal risks and helps develop controls and contingencies.
Confusion: Risk management increases organizational visibility across all relationship stages.
In addition, an effective TPRM program increases security, trust and reporting capabilities.
How do you determine vendor risk?
The risks associated with your vendors would be any that you have discovered during your security review process of the vendor that you are monitoring, tracking, treating or accepting as you are in business with this vendor. These typically fall into the categories of Profiled Risk, Inherent Risk, or Residual Risk. For example: “Vendor has a password policy that does not meet our internal policy requirements for passwords.”
Once a risk is identified, determine the appropriate treatment plan. In the example above, this might be: “Vendor will implement stronger password policy by Q1/Q2.
Automate Your Journey
Drata's platform experience is designed by security and compliance experts so you don't have to be one.
Close more sales and build trust faster while eliminating hundreds of hours of manual work to maintain compliance.