How to Build a Trust Center that Delivers Growth
Here are a few best practices for establishing your security posture to generate demand across enterprise buyers.
The buyer’s journey has fundamentally changed for B2B SaaS. Traditionally, purchasing decisions were finalized by key executives and end users, and vendors only underwent an infosec review as a final “formality.” Now, infosec has become an initial stage that buyers use to screen vendors before even considering them.
In this new landscape, a Trust Center serves as a critical first impression, yet it remains underutilized and often poorly maintained, making it a missed opportunity—especially for startups. A well-managed Trust Center can significantly enhance credibility and attract enterprise buyers from the outset.
Underutilization of Trust Centers
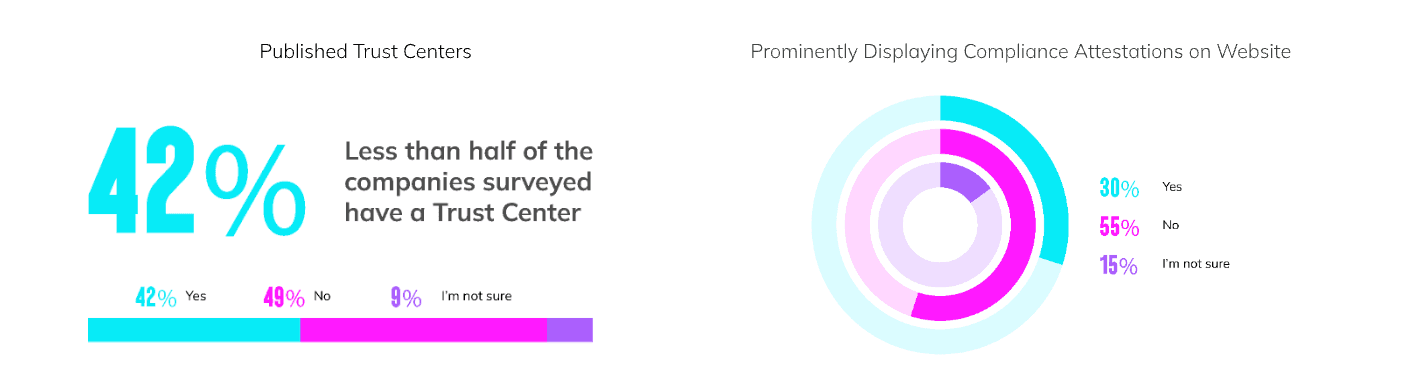
For startups, compliance is less about risk mitigation and more about establishing credibility for enterprise sales; however, a significant number of companies fail to effectively highlight their security posture. At Eden Data, we recently surveyed high-growth organizations about their compliance journeys and found that just 42% are using a Trust Center and fewer than one in three prominently display their compliance attestation on their website.
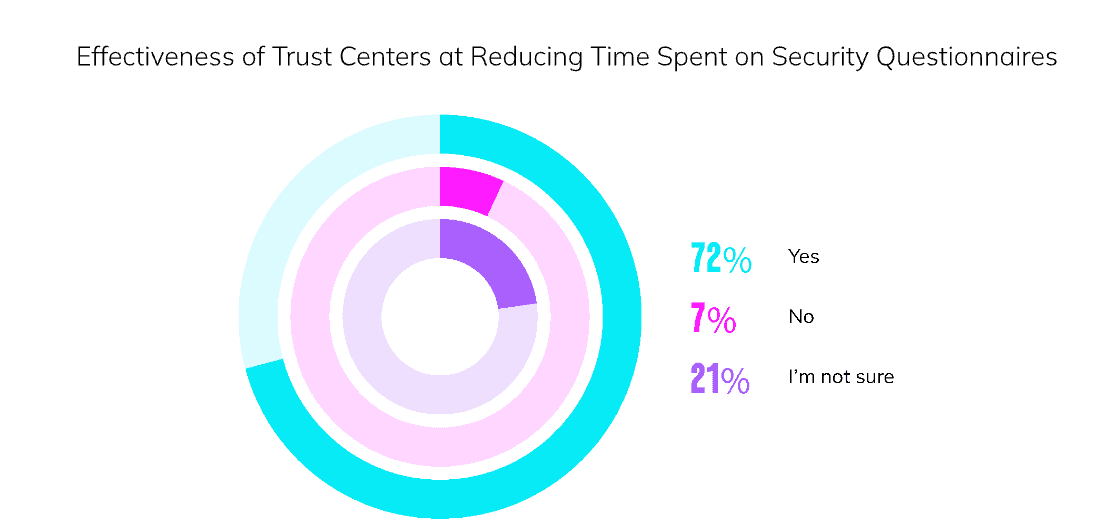
Of respondents with Trust Centers, nearly three-quarters said that their Trust Center effectively reduces the time spent on security questionnaires.
The absence of a Trust Center or visible compliance attestations on a website are a missed opportunity, and something we stress to our clients upon achieving compliance. A Trust Center serves as a centralized repository of a company’s security and compliance certifications, offering easy access to critical information about its security posture and compliance frameworks. Additionally, a Trust Center saves time by consolidating information that would require input from multiple departments. It enhances the perception of a company's commitment to security by presenting its measures in a professional and organized manner.
Configuring a Trust Center
Drata's Trust Center helps organizations streamline security reviews and demonstrate their commitment to security. It allows companies to automate the sharing of security documents, display real-time compliance statuses across frameworks, and manage access to security information. This feature is designed to accelerate sales cycles by providing transparency and reducing the time spent on security questionnaires, thereby enhancing trust with partners and customers. It integrates seamlessly with the rest of Drata’s platform, allowing for continuous control monitoring and automated evidence collection.
Our cybersecurity and compliance firm is Drata’s Partner of the Year for both 2022 and 2023. We asked our team of ex-Big 4 compliance professionals what advice they give to the 200+ brands we’ve helped achieve audit-readiness rapidly:
What to include: A Trust Center should feature key compliance reports such as SOC 2, ISO 27001, and any other relevant attestations or certifications. It's beneficial to include security reports, penetration test results, descriptions of security controls, policy documentation, and details on continuous monitoring efforts. Information about subprocessors, a summary of security practices, architecture diagrams (appropriately redacted), and privacy policies can also be valuable. Additionally, featuring any high-level security practices, bug bounty program details, and relevant announcements can help showcase your organization’s commitment to security and transparency.
What not to include: Avoid including any confidential customer or business data, sensitive internal documents, or detailed network architecture that could expose potential security vulnerabilities. Do not share information that is too revealing, such as specific tooling details, internal procedures, or failing security tests. It's also advisable to exclude employee-specific information, outdated content, or overly detailed security policies and monitoring statuses that could create unnecessary noise or raise concerns.
Where to link to your Trust Center: To make the Trust Center easily accessible, label it clearly as "Security Trust Center" or "Security Center" and place the link in a prominent location, such as the top navigation menu alongside sections like “Company,” “About,” or “Legal.” Also, ensure it's included in the footer near the Terms of Service (ToS) and Privacy Notice. The subdomain URL should be simple and direct, such as www.trust.yourcompany.com. Consider using icons like a shield or lock to make the link stand out, and promote the Trust Center and any new certifications through social media to increase visibility and awareness.
Want to Learn More?
Eden Data conducted a survey among high-growth organizations to evaluate how investing in compliance frameworks like SOC 2, ISO 27001, GDPR, and others impacts their business. Check out all the insights by downloading our report on ROI of Compliance.