CIS Controls v8.1
Strengthen your security posture and mitigate the most common cyber-attacks with CIS Controls v8.1’s defense-in-depth using Drata’s automated control mapping and continuous evidence collection.
Strengthen your security posture and mitigate the most common cyber-attacks with CIS Controls v8.1’s defense-in-depth using Drata’s automated control mapping and continuous evidence collection.
Accelerate Your CIS Controls v8.1 Journey

Excellent Based on 1000+ Reviews
Drata for CIS Critical Security Controls
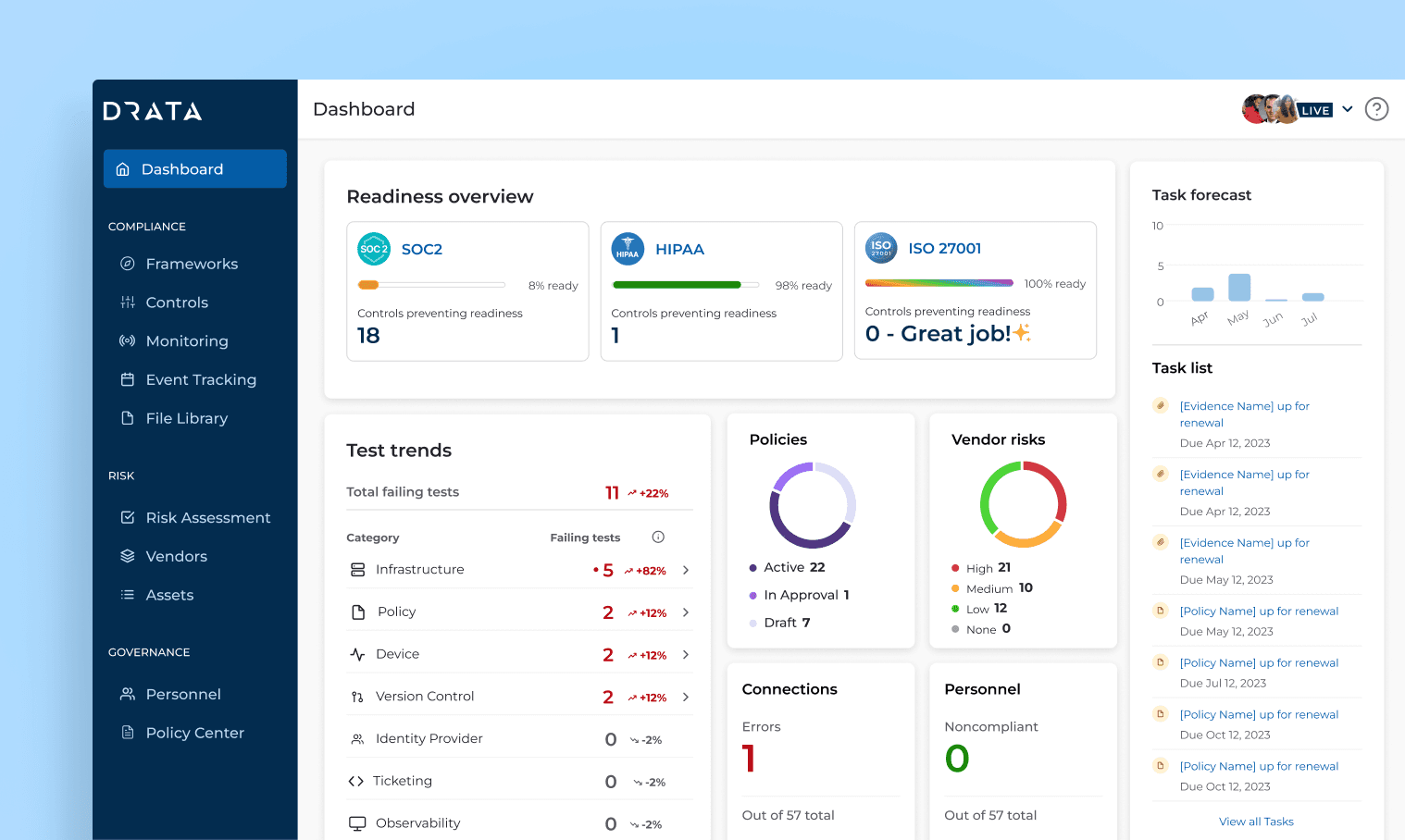
Simplify CIS Controls v8.1 adoption with intuitive guides and automation.
Drata’s platform, ranked highest for ease of use on G2, enables rapid compliance without the hassle with out‑of‑the‑box artefacts for 153 Requirements, DCF‑mapped controls, tailored policy templates, continuous monitoring (Autopilot), test mapping, and control readiness dashboards.
Stay ahead of emerging threats and evolving compliance standards with continuous updates to frameworks and proactive risk management tools including Drata’s Risk Management Module, Vendor Risk Management (TPRM), Trust Center, and Requirements Library.

Drata supports Evidence guidance Level 2 for CIS Controls v8.1 and automatically collects evidence, so you can say goodbye to screenshots and spreadsheets.

Drata's 24/7 continuous control monitoring ensures you stay compliant and gives you full visibility into your status at all times.

Build trust. Show your commitment to foundational security through CIS Controls v8.1 by sharing your practices with Drata's Trust Center

Drata’s built-in self-assessments enable you to efficiently report on your security program’s effectiveness.

Choose from Drata's controls or create custom controls to meet your specific needs and framework requirements.

Drata’s support team consists of compliance experts and former auditors. Our experts are a click away.
Customers
Don’t Take Our Word for It
See why companies like you love using Drata.
Resources
Looking for more?
Discover the latest compliance resources and jumpstart your GRC program today.
Frequently Asked Questions
What is CIS 8..1?
The Center for Internet Security (CIS) Critical Security Controls® v8.1 are a prioritized, community‑developed set of 18 high‑level security controls (with 153 individual Safeguards) that form a practical, defense‑in‑depth roadmap for mitigating the most common cyber‑attacks. They evolved from the original SANS Top 20 list into a flexible framework that now aligns to NIST CSF functions and scales from small businesses to large enterprises.
What are CIS Controls?
CIS Controls are a prioritized set of best practices developed to mitigate the most common cybersecurity risks, scalable for organizations of all sizes.
Who manages CIS Controls?
The framework is maintained by the non-profit Center for Internet Security, with input from global cybersecurity experts.
Are CIS Controls mandatory?
CIS Controls are voluntary but highly recommended as a foundational cybersecurity measure with significant market-driven expectations.
Can CIS Controls help with other frameworks?
Yes, CIS Controls map directly to frameworks like SOC 2, ISO 27001, and NIST, streamlining multi-framework compliance.
What is the Drata advantage for CIS Controls?
Drata offers comprehensive, automated compliance support including continuous monitoring, automated evidence collection, and ready-to-use policy templates.