Automate Compliance. Streamline Security. Manage Risk.
From startup to enterprise, Drata keeps you ahead of security reviews, audits, and risks.
What are you interested in?
Trusted by 7,000 Global Customers











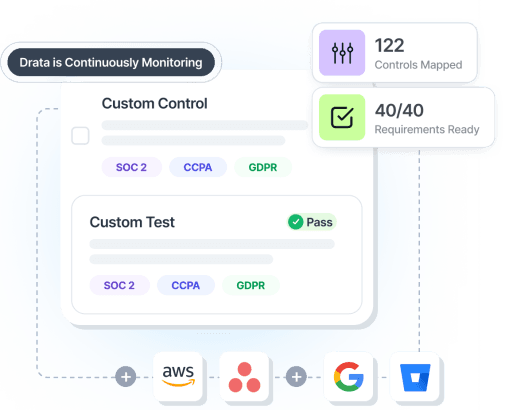
Compliance at Every Stage
Achieve GRC Goals Faster
Getting started, looking to scale GRC, or want to enhance your security compliance program? Drata meets you where you are in your journey.
Why Use Drata?
Security Without Compromise
Don’t choose between automation and configurability. See how Drata enables both for complete control over your GRC journey.
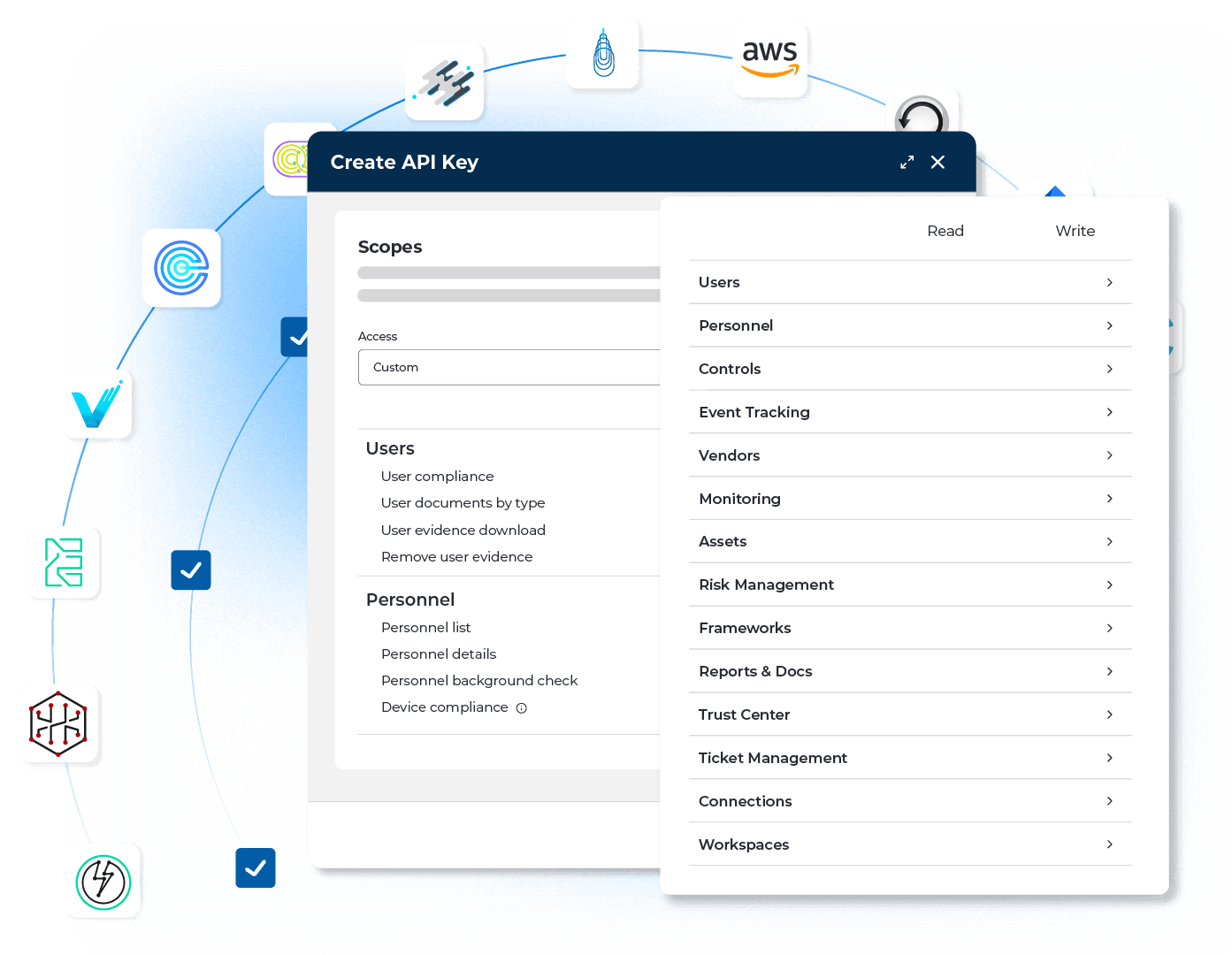
Integrate with More Systems
With hundreds of native integrations, you can connect your HRIS, SSO, cloud provider, DevOps toolchain, and countless other systems to Drata—opening endless possibilities for control enforcement, monitoring, evidence collection, and remediation.
Want to validate a specific control or connect to a different tool? Use our Open API to build deep, custom integrations with any system.
Configure Compliance Your Way
Compliance looks different for every company. That’s why Adaptive Automation offers complete configurability.
With deeper integrations and more testing sources, Adaptive Automation lets you build no-code tests with custom logic to automate and customize your control monitoring.
Automate Evidence Collection
Collect all of the evidence you need, without the manual work. Between custom tests, integration coverage and our API, you can automatically gather more evidence without taking screenshots or managing evidence in spreadsheets.
Control the Process
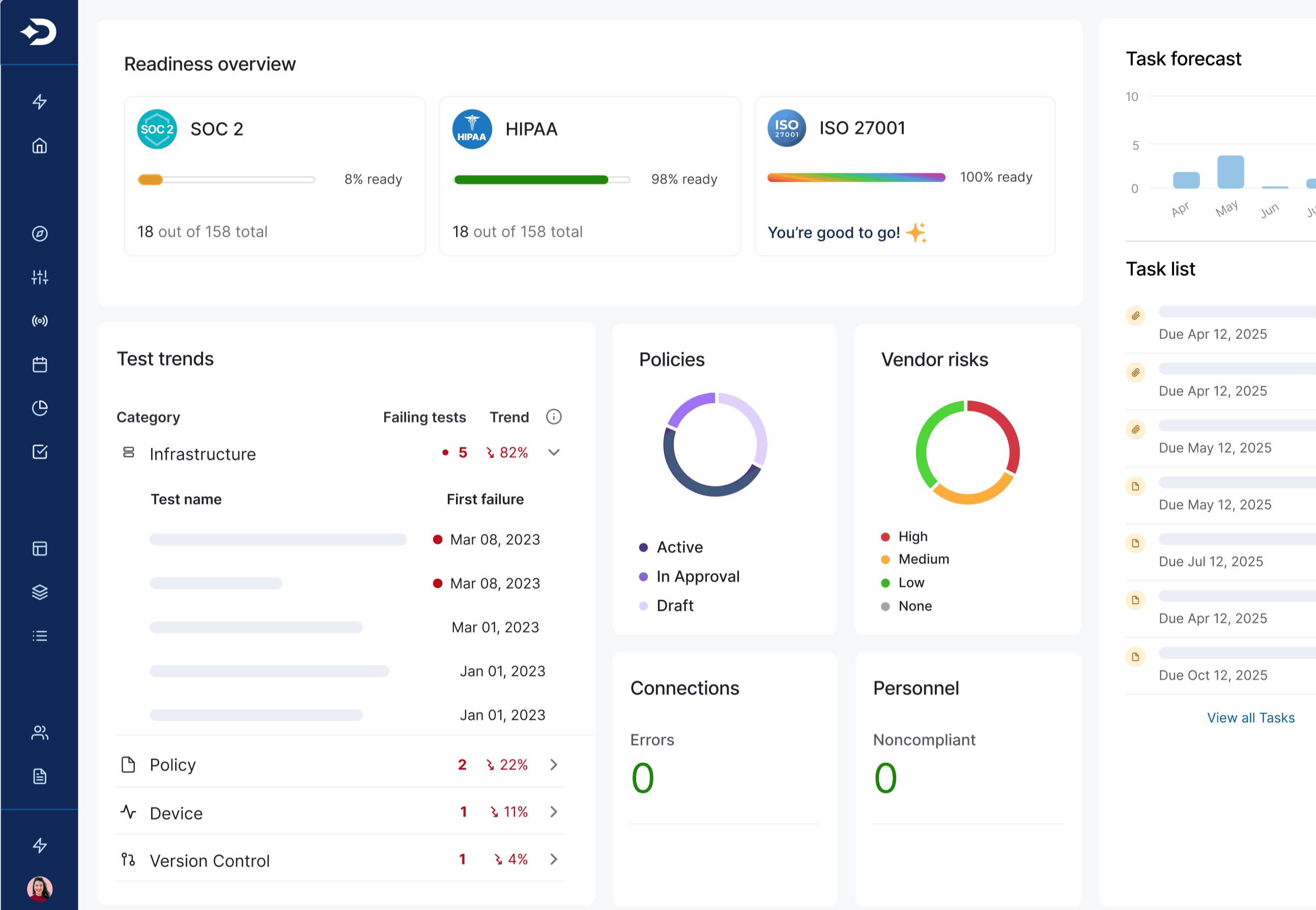
With all your evidence, controls, and documents in one place, you can manage every step of the process. Continuous control monitoring provides full visibility into your compliance status so you can stay on top of risks and action items.
Quickly create tasks and manage tickets to ensure key compliance work doesn’t fall through the cracks. And with role-based access, you can protect sensitive data and streamline work.

Excellent Based on 1000+ Reviews
Put Security & Compliance on Autopilot®
Get Started With Frameworks
Enjoy Automation Without Sacrificing Customization
20+ frameworks, designed to help you achieve and maintain compliance faster.

SOC 2
SOC 2 defines criteria for managing data based on: security, availability, processing integrity, confidentiality, and privacy.

ISO 27001
ISO 27001 is an information security management system (ISMS) that helps keep consumer data safe.

HIPAA
HIPAA is a law requiring organizations that handle protected health information (PHI) to keep it protected and secure.

GDPR
GDPR is a regulation in EU law on data protection and privacy in the European Union and the European Economic Area.

PCI DSS
PCI DSS is a set of controls to make sure companies that handle credit card information maintain a secure environment.

Cyber Essentials
Cyber Essentials helps companies guard against the most common cyber threats and demonstrate commitment to cyber security.
NIST AI RMF
Safely navigate the implementation and usage of artificial intelligence with this risk management framework.

CCPA
CCPA gives consumers control over the personal information that businesses collect and guidance on how to implement the law.

CMMC
CMMC is a unified standard for implementing cybersecurity across the defense industrial base (DIB).

Microsoft SSPA
SSPA sets privacy and security requirements for Microsoft suppliers and drives compliance to these requirements.

NIST CSF
National Institute of Standards and Technology’s framework for Improving Critical Infrastructure Cybersecurity (CSF).

NIST SP 800-53
NIST SP 800-53 is a catalog of controls for all U.S. federal information systems except those related to national security.

NIST SP 800-171
NIST SP 800-171 recommends requirements for protecting the confidentiality of controlled unclassified information (CUI).

ISO 27701
ISO 27701 specifies requirements for establishing and continually improving a privacy information management system.

FFIEC
The FFIEC provides a set of technology standards for online banking that financial institutions must follow.

CCM
The Cloud Controls Matrix by Cloud Security Alliance (CSA) is a cybersecurity control framework for cloud computing.

FedRAMP
FedRAMP compliance and authorization enables SaaS companies (referred to as CSPs) to work with federal government agencies.
NIS 2
NIS 2 Directive is a EU-wide cybersecurity law that improves the resilience and incident response across the European Union.

DORA
Digital Operational Resilience Act (DORA) ensures EU financial entities are resilient to information and communication technology (ICT) disruptions.
The Highest-Rated Cloud Compliance Platform

G2 Best Software Awards
For the second consecutive year, Drata has earned top marks in G2’s annual Best Software Awards, with recognition in categories like GRC, Security, Highest Satisfaction, and more.
The Open Compliance Revolution
The compliance journey started with screenshots. Now, Drata is ushering in a new era of trust, automation, and openness. We’ve put the power in our customers' and partners' hands, and we'll be alongside you every step of the way.
Looking For More?
Check Out the Latest GRC Resources
Automate Your Journey
Drata's platform experience is designed by security and compliance experts so you don't have to be one.
Connect
Easily integrate your tech stack with Drata.
Configure
Pre-map auditor validated controls.
Comply
Begin automating evidence collection.
Put Security & Compliance on Autopilot®
Close more sales and build trust faster while eliminating hundreds of hours of manual work to maintain compliance.