HIPAA vs. HITRUST: Key Differences Explained
HIPAA is a legal requirement enforced by the U.S. government that regulates how you handle patient data. HITRUST CSF is a third-party audit and certification process that incorporates aspects of HIPAA in addition to NIST, ISO, PCI DSS, and more.
There’s more than one approach to protecting patient health information. The most popular frameworks among organizations in the healthcare industry are HIPAA and HITRUST CSF.
HIPAA is a legal requirement enforced by the U.S. government that regulates how you handle patient data. HITRUST CSF is a third-party audit and certification process that incorporates aspects of HIPAA in addition to NIST, ISO 27001, PCI DSS, and more.
Below, we’ll break down the differences between HITRUST vs. HIPAA and highlight when you might want to consider one over the other.
What’s the Difference Between HITRUST vs. HIPAA?
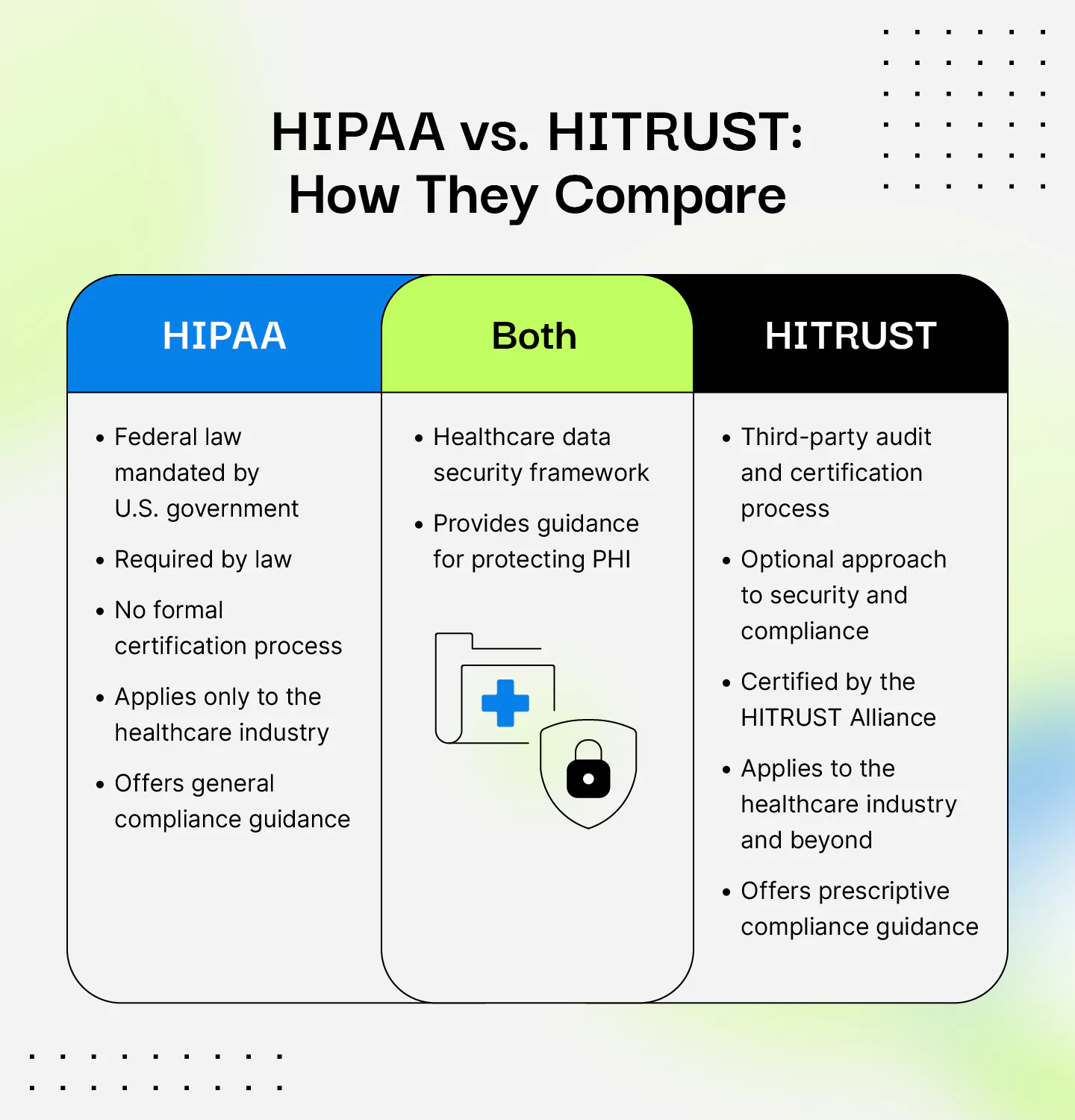
One of the main differences between HITRUST and HIPAA is that HITRUST CSF is a global security and risk management framework that reaches beyond the healthcare industry. HIPAA, on the other hand, is a U.S. law that governs how patient health information should be protected.
HIPAA includes specific rules for processing, storing, and transmitting patient health information (PHI). HITRUST is a more flexible framework organizations can use to achieve compliance with HIPAA and other common frameworks.
If you’re non-compliant with HIPAA, repercussions include hefty fines and even jail time. There is no specific penalty for non-compliance with HITRUST, as it’s an optional approach to compliance, not a government-regulated law like HIPAA.
Another important distinction between HIPAA and HITRUST is that HITRUST is a certifiable framework, meaning you can actually become HITRUST certified by the HITRUST Alliance. With HIPAA, there’s no certification process. In order to be compliant, you must regularly review your compliance with HIPAA, which may include engaging a third-party auditor to assess your security posture.
In terms of the breadth of each framework, HITRUST is more comprehensive than HIPAA. This is because HIPAA is specific to the healthcare industry, whereas HITRUST is industry agnostic and can be used by organizations across all industries.
What Is HITRUST?
HITRUST is governed by the HITRUST Alliance, an independent organization established in 2007.
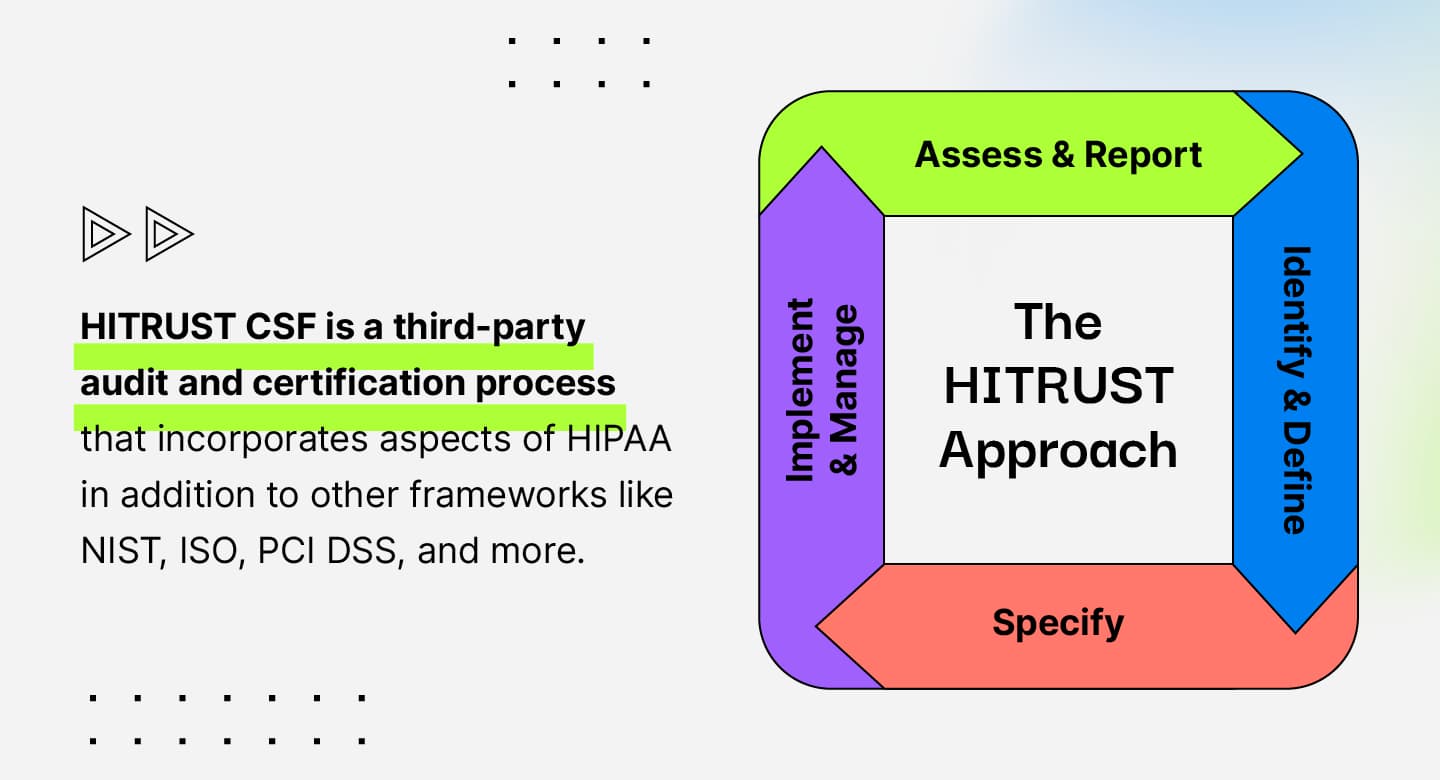
The HITRUST Common Security Framework (CSF) pulls elements of common compliance and risk management regulatory frameworks into one flexible framework. Frameworks used within HITRUST CSF include:
NIST
ISO 27001/27002
PCI DSS
GDPR
CMMC
COBIT
HITRUST CSF was designed to be adaptable for organizations regardless of their industry, size, systems, and compliance requirements. Every organization has a unique security control set based on scope, where riskier businesses have more stringent requirements.
How To Achieve HITRUST Compliance
Unlike HIPAA or SOC 2, HITRUST CSF is a certifiable framework.
Organizations can become HITRUST certified through a process called validated assessment. This involves working with an authorized external assessor to conduct an audit of your security practices. Results are then submitted to the HITRUST Alliance for review and certification.
What Is HIPAA?
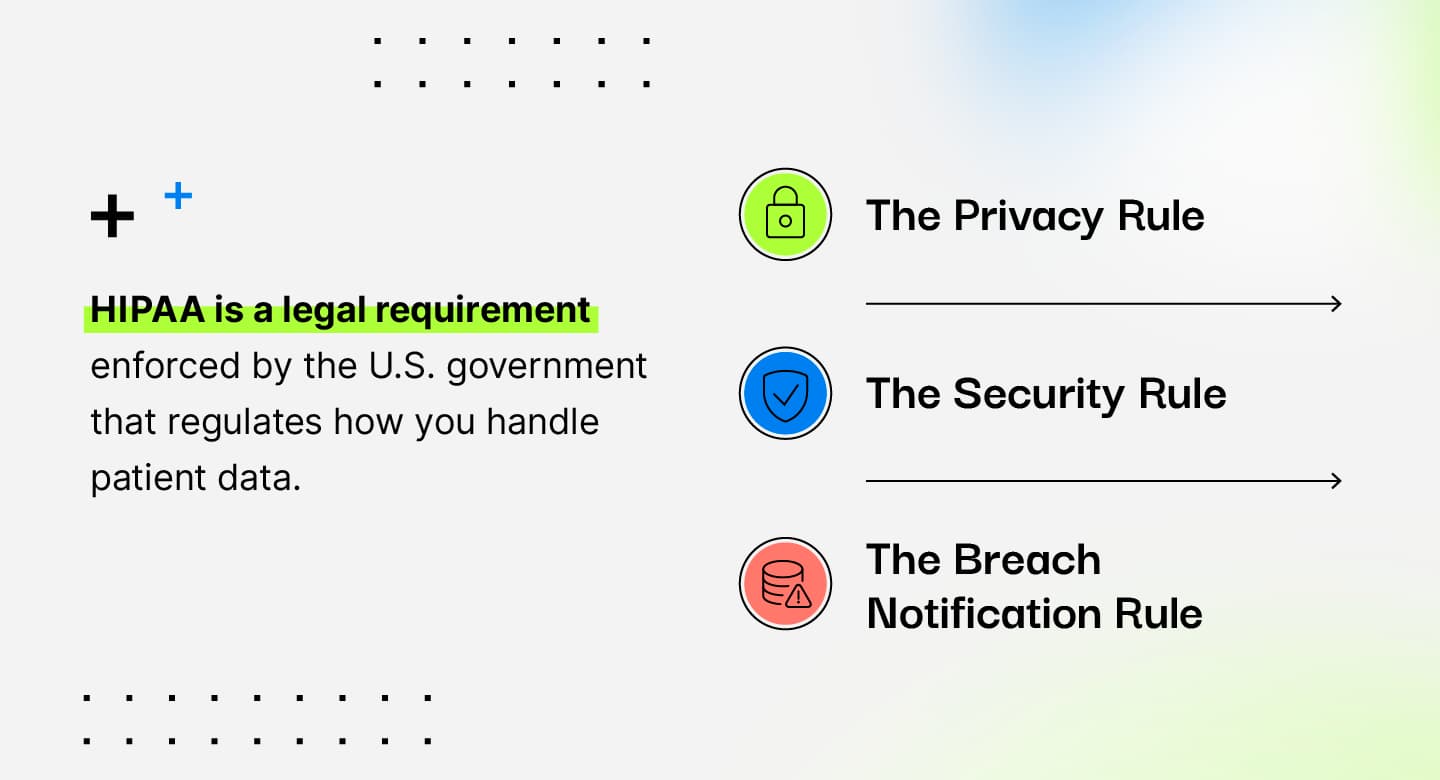
HIPAA (which stands for the Health Insurance Portability and Accountability Act) is a U.S. law passed by Congress in 1996 that sets the legal standard for patient health data protection.
HIPAA applies to covered entities and business associates. A covered entity is a health plan, healthcare clearinghouse, or healthcare provider. Business associates are organizations or individuals that use or disclose PHI on behalf of, or to provide services to, a covered entity. Common examples of business associates include accountants, lawyers, cloud storage providers, and billing companies.
The law is broken up into several rules:
The Security Rule outlines the physical, technical, and administrative safeguards organizations must have in place to be compliant.
The Privacy Rule outlines how protected health information can be used and shared.
The Breach Notification Rule outlines how organizations must handle patient information leaks.
How To Achieve HIPAA Compliance
The exact requirements for your organization will depend on the nature of your business, its size, and complexity. All covered entities and business associates must be HIPAA compliant, but how they comply may look different.
To comply with HIPAA, you can expect to:
Conduct annual self-audits to look for gaps in compliance.
Create and implement remediation plans based on the gaps you uncover in self-audits.
Document policies and procedures mapping to the HIPAA rules.
Hold annual staff training on your policies and procedures.
Obtain business associate agreements with all applicable vendors.
Create an incident management plan in accordance with the Breach Notification Rule.
For a step-by-step look at what it takes to become HIPAA compliant, check out at our HIPAA compliance checklist.
Similar to SOC 2, HIPAA does not have a formal compliance certification process. To prove compliance, you’ll need to hire an audit firm to conduct an audit and provide an attestation. Failure to comply with HIPAA can result in violations in the form of hefty fines or, in more severe instances, jail time.
Does HITRUST Compliance Equal HIPAA Compliance?
HITRUST compliance doesn’t necessarily equal HIPAA compliance. There’s a chance you could be compliant with HITRUST but violate one or more of the HIPAA requirements.
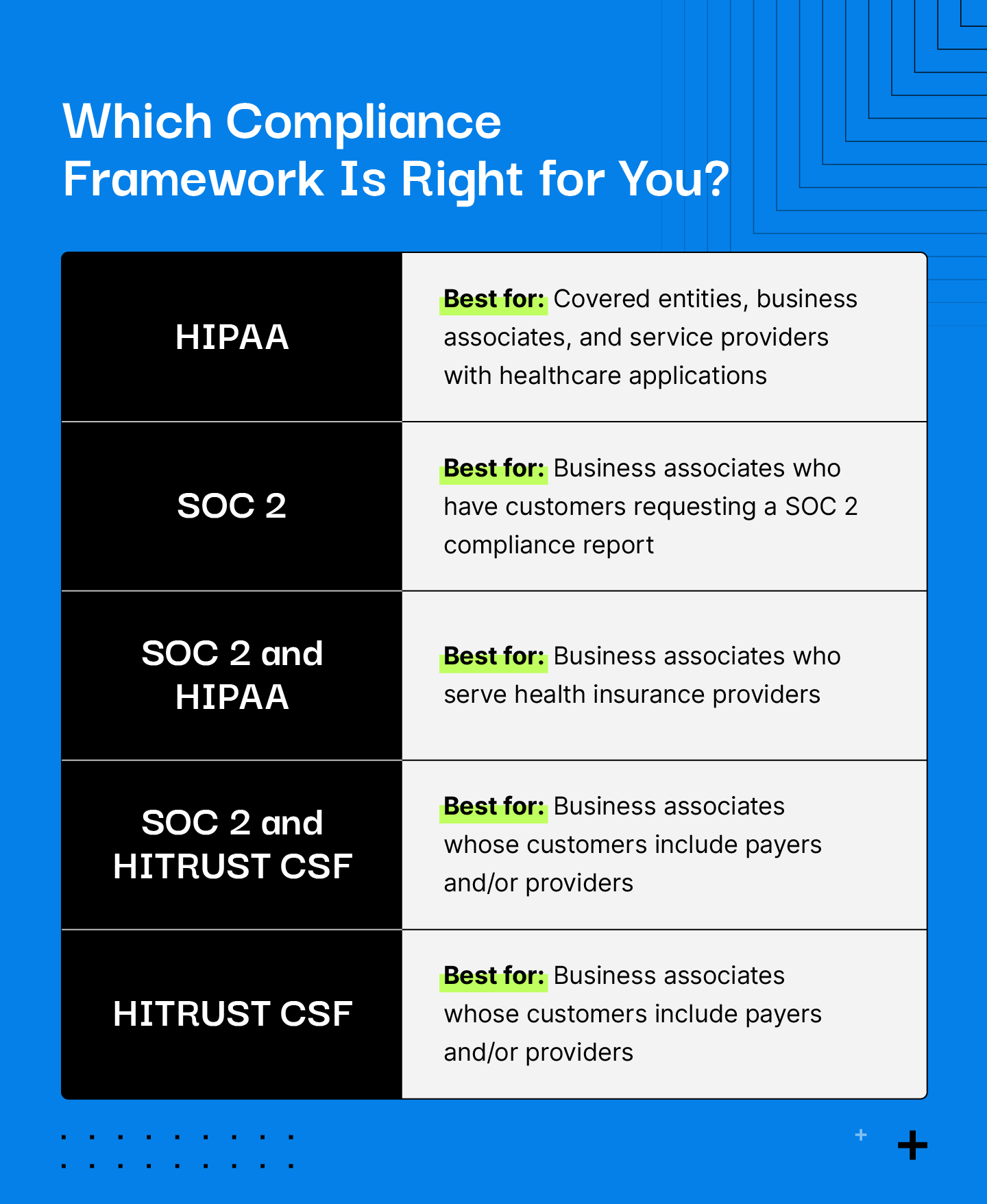
HITRUST vs. HIPAA: Which To Choose
While any business that’s considered a covered entity or business associate must comply with HIPAA, how you choose to demonstrate compliance is up to you.
HITRUST isn’t the only framework you can use to work toward HIPAA compliance, but it is a popular one within the healthcare industry. According to HITRUST, 80% of hospitals and 85% of healthcare insurers use HITRUST CSF to achieve compliance.
You may find that the general guidance outlined in the HIPAA law isn’t as prescriptive as you’d like. HITRUST helps bridge the gap between what’s stated in the law and how that applies to your organization with specific controls tailored to your specific situation.
Additionally, if you’re a business associate who works with clients in various industries outside of the healthcare industry, HITRUST can be an ideal solution that helps you achieve not just HIPAA compliance, but compliance with other popular frameworks like NIST, PCI DSS, and ISO, to name a few.
How Drata Can Help You Streamline HIPAA Compliance
No matter how you choose to approach HIPAA compliance, the process can be taxing. That’s why a compliance automation tool like Drata can come in handy.
We can help you plan, automate, and track your HIPAA compliance program and support you along every step of your compliance journey. Schedule a demo today to see how we can help.
The Universal Operational Challenge
Discover why established and enterprise companies indicate the most significant risk to their businesses are third parties.
In recent years there has been a significant rise in cybersecurity related supply chain attacks, now even overtaking the damage done by malware by more than 40% in 2022 alone. As part of that increase, there were 10 million people impacted by supply chain attacks that targeted 1,743 entities. With this in mind, Drata developed a study designed to tap the pulse of commercial and enterprise organizations to determine what, if any, impact existing processes associated with managing third parties have on the business, how they are set to change in the next two years, and the level of risk associated with them.
By surveying 300 established and enterprise organizations, we identified optimistic security teams who feel prepared to manage these risks and those who see the associated blind spots with third parties are a cause for concern. From these insights and others, a single theme emerged: Third parties are a universal operational challenge.